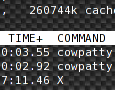
 As the market with CPU has moved to multi-core solutions as a alternative method to increase computation power, intensive computing applications are not adapting to this fact so quickly. A Lot of people still don’t know that the system is not able to split tasks into more threads and distribute the work evenly upon the cores. This task is on the application developer who has to implement the multi-thread supporting mechanism.
As the market with CPU has moved to multi-core solutions as a alternative method to increase computation power, intensive computing applications are not adapting to this fact so quickly. A Lot of people still don’t know that the system is not able to split tasks into more threads and distribute the work evenly upon the cores. This task is on the application developer who has to implement the multi-thread supporting mechanism.
Content for ‘Pentest’
 From the word compound of evil and grade, you see there will be something evil about this piece of software and upgrades. It is a modular framework for supplying clients with fake updates that can contain a wide scale of payloads. The problem of poorly implemented actualization routines has been well know for quite some time now, but it seems it has been greatly overlooked. In the time of creation Evilgrade (summer 2008), very popular software has been vulnerable to this kind of exploit such as
From the word compound of evil and grade, you see there will be something evil about this piece of software and upgrades. It is a modular framework for supplying clients with fake updates that can contain a wide scale of payloads. The problem of poorly implemented actualization routines has been well know for quite some time now, but it seems it has been greatly overlooked. In the time of creation Evilgrade (summer 2008), very popular software has been vulnerable to this kind of exploit such as
 After demonstrating and still tweaking the nervously expected BackTrack 4 beta at shmoocon, it is now available for download from some number of official mirrors. There are several torrents named bt4 but believe they are full of malware. The Remote-Exploit encourages you to download it directly from them. They have made a big decision on this version – moved from from Slackware to (as we have seen) an Ubuntu server with
After demonstrating and still tweaking the nervously expected BackTrack 4 beta at shmoocon, it is now available for download from some number of official mirrors. There are several torrents named bt4 but believe they are full of malware. The Remote-Exploit encourages you to download it directly from them. They have made a big decision on this version – moved from from Slackware to (as we have seen) an Ubuntu server with
 Security conference PACSEC 2008 that will be held in japanese Tokyo on 12th and 13th November 2008 has a great attraction. There will be presented a security research from Mark Tew as a next (not brute force), new implementation of the WPA-TKIP attack. WPA-TKIP security based on the dynamic key generation was supposed to be by laicks and professionals as unbreakable. Much more safe then funny WEP encription.
Security conference PACSEC 2008 that will be held in japanese Tokyo on 12th and 13th November 2008 has a great attraction. There will be presented a security research from Mark Tew as a next (not brute force), new implementation of the WPA-TKIP attack. WPA-TKIP security based on the dynamic key generation was supposed to be by laicks and professionals as unbreakable. Much more safe then funny WEP encription.
 Every press on the keyboard pruduces a small impuls of electromagnetic radiation. This radiation can be captured and easy (quickly) decoded. Even though the described attack effects only some keyboard models it is worth mentioning. Before the penetration test there was done a verification of eleven different keyboards. Each one was reciptive to one of four different methods of availabe attacks. As result see the videos bellow.
Every press on the keyboard pruduces a small impuls of electromagnetic radiation. This radiation can be captured and easy (quickly) decoded. Even though the described attack effects only some keyboard models it is worth mentioning. Before the penetration test there was done a verification of eleven different keyboards. Each one was reciptive to one of four different methods of availabe attacks. As result see the videos bellow.
 Last year we told about not so well know tool called MDK, as part of the “Cracking WEP key – Acces Point with pree-shared key (PSK” concept. Alot of time has passed by since then and now we have well workiong stable version even with GUI extension Charon. It was not much of a deal in Fall 2007, but the situation has changed. The autor has also decidedd to eneble the Destruction Mode in the menu.
Last year we told about not so well know tool called MDK, as part of the “Cracking WEP key – Acces Point with pree-shared key (PSK” concept. Alot of time has passed by since then and now we have well workiong stable version even with GUI extension Charon. It was not much of a deal in Fall 2007, but the situation has changed. The autor has also decidedd to eneble the Destruction Mode in the menu.
 This is second part of pentesting how to (Ultimate Ubuntu Guide). Lessons from 1 to 9 you can find at How to crack WEP. In this part we ‘ll continue with technique called korek chopchop attack, wep key cracking, aireplay-ng examples, rejects open-system authentication, packetforge-ng, 5GHz band (including frequency and modularity information) , WPA (WPA-PSK) cracking abstrack, connecting to network (gateway, internet) and epilogue
This is second part of pentesting how to (Ultimate Ubuntu Guide). Lessons from 1 to 9 you can find at How to crack WEP. In this part we ‘ll continue with technique called korek chopchop attack, wep key cracking, aireplay-ng examples, rejects open-system authentication, packetforge-ng, 5GHz band (including frequency and modularity information) , WPA (WPA-PSK) cracking abstrack, connecting to network (gateway, internet) and epilogue
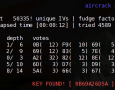
 WLAN Hacking – WPA-PSK handshake. The deauth atack with Aireplay-ng -0 wants to disconect the client from Access Point and after reconnecting get by tapping the handshake. But the process fails. Now what? Be aware that there is another (maybe better and easier) way how to get the data for crack WPA. Wireshark is a strong application and the technology that will be described can be used in other ways like for universal sniffing of the net traffic.
WLAN Hacking – WPA-PSK handshake. The deauth atack with Aireplay-ng -0 wants to disconect the client from Access Point and after reconnecting get by tapping the handshake. But the process fails. Now what? Be aware that there is another (maybe better and easier) way how to get the data for crack WPA. Wireshark is a strong application and the technology that will be described can be used in other ways like for universal sniffing of the net traffic.


