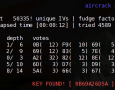
 New lzm pack released. What is Aircrack? Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the all-new PTW attack, thus making the attack much faster compared to other WEP cracking tools. In fact, Aircrack-ng is a set of tools for auditing wireless networks.
New lzm pack released. What is Aircrack? Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the all-new PTW attack, thus making the attack much faster compared to other WEP cracking tools. In fact, Aircrack-ng is a set of tools for auditing wireless networks.
Katalog pro September, 2008
 At airdump.net there are altogether pentest and security tutorials. This text will reflex who to after securing oneselfs installation get the overview what is happening in the system. There is a lot of tricks. We will demonstrate how to do it easily and all together. The text was created to show way of GUI monitoring, mainly firewall and network events. Speaking generally the configuration possibilities are much more wider. Read more..
At airdump.net there are altogether pentest and security tutorials. This text will reflex who to after securing oneselfs installation get the overview what is happening in the system. There is a lot of tricks. We will demonstrate how to do it easily and all together. The text was created to show way of GUI monitoring, mainly firewall and network events. Speaking generally the configuration possibilities are much more wider. Read more..
 BlueTooth Hacking. The text will be continuously completed with pictures and links for download. BlueTooth is a great technology that is implemented in several mobile device. For communication with other device no cable is necessary and there is a lot of applications dedicated directly for Bluetooth. As well as in the case with WiFi there is not necessary a cable for connecting two devicees. Expansion of Symbian based mobile phones will probably bring into this sector many new possibilities.
BlueTooth Hacking. The text will be continuously completed with pictures and links for download. BlueTooth is a great technology that is implemented in several mobile device. For communication with other device no cable is necessary and there is a lot of applications dedicated directly for Bluetooth. As well as in the case with WiFi there is not necessary a cable for connecting two devicees. Expansion of Symbian based mobile phones will probably bring into this sector many new possibilities.
 Complete Google Hacks List (and some more) is moved here from the comment. I hope ‘ll ensemble older short list of examples for efective search (hacking google). Sometimes you want to find all of your search terms in a document, and sometimes you want to find either one term or another. The term for this type of search is “Boolean.” The term “Boolean” comes from Nineteenth Century mathematician George Boole. “Boolean logic” is something that is used in all sorts of computing applications, not just search engines. Thx to handymann81
Complete Google Hacks List (and some more) is moved here from the comment. I hope ‘ll ensemble older short list of examples for efective search (hacking google). Sometimes you want to find all of your search terms in a document, and sometimes you want to find either one term or another. The term for this type of search is “Boolean.” The term “Boolean” comes from Nineteenth Century mathematician George Boole. “Boolean logic” is something that is used in all sorts of computing applications, not just search engines. Thx to handymann81
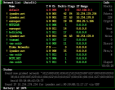 Updated. Now Windows browser Internet Explorer supported! It’s accessable interactive WiFi WarDriving Map of Access Points with search. English is not necessary. Most of record (at this time) is in the Prague (Czech Republic, Europe) so don’t search other places. The new database search is complete. The database search is now linked to map. Just click in search result on arbitrary row and you will be switched to map to see the locality of Access Point.
Updated. Now Windows browser Internet Explorer supported! It’s accessable interactive WiFi WarDriving Map of Access Points with search. English is not necessary. Most of record (at this time) is in the Prague (Czech Republic, Europe) so don’t search other places. The new database search is complete. The database search is now linked to map. Just click in search result on arbitrary row and you will be switched to map to see the locality of Access Point.
 Linux application cracking. What for it is? Primarily the application run can be understund. Not all Linux software is free (Macintos ? :). That could be for someone a challange and he can “converte” the application on freeware.
Linux application cracking. What for it is? Primarily the application run can be understund. Not all Linux software is free (Macintos ? :). That could be for someone a challange and he can “converte” the application on freeware.
This experience can be used on other systems (Windows). With this knowledge you will be able to precisely tune applications and gain control on new boxes.
 Did you forget your Admin Windows XP password? High-level user will choose application Ophcrack. This GUI application is Windows password cracker. It uses rainbow tables and needs some time. For more elegant and direct solution use older and almost forgotten application – CIA Commander. Image. After start Application CIA Commander it makes do with one floppy disc which is formated. Later the necessary parts of the application are recorded.
Did you forget your Admin Windows XP password? High-level user will choose application Ophcrack. This GUI application is Windows password cracker. It uses rainbow tables and needs some time. For more elegant and direct solution use older and almost forgotten application – CIA Commander. Image. After start Application CIA Commander it makes do with one floppy disc which is formated. Later the necessary parts of the application are recorded.
 I’m sure you know security and pentesting videos and video tutorials on server irongeek, youtube, google video etc. Sooner or later you will find a problem that is hard to be describe online or vice versa. But you are the one who nows the solution and you want to share it. If you are planning to do your own clip the tutorial how to make your own video will show you how to easily make a sound video shot or a picture sequence.
I’m sure you know security and pentesting videos and video tutorials on server irongeek, youtube, google video etc. Sooner or later you will find a problem that is hard to be describe online or vice versa. But you are the one who nows the solution and you want to share it. If you are planning to do your own clip the tutorial how to make your own video will show you how to easily make a sound video shot or a picture sequence.


