 As the market with CPU has moved to multi-core solutions as a alternative method to increase computation power, intensive computing applications are not adapting to this fact so quickly. A Lot of people still don’t know that the system is not able to split tasks into more threads and distribute the work evenly upon the cores. This task is on the application developer who has to implement the multi-thread supporting mechanism.
As the market with CPU has moved to multi-core solutions as a alternative method to increase computation power, intensive computing applications are not adapting to this fact so quickly. A Lot of people still don’t know that the system is not able to split tasks into more threads and distribute the work evenly upon the cores. This task is on the application developer who has to implement the multi-thread supporting mechanism.
Some of the applications we would like to run on multiple cores are coWPAtty, genPMK and airolib-ng. With a little guide and comparison test, we will show you how to do it. Our processor is dual-core Intel Core2Duo clocked to 2.23GHz. For load information we will use the top command and the files to crack, we will use the files (handshake capture and word-list) already distributed with coWPAtty. Just to be complete, we are running a bit modded BackTrack 3 Linux.
Test 1 – Regular dictionary attack on the WPA key with coWPAtty
cowpatty -r /root/wpapsk-linksys.dump -f /root/dict -s linksys
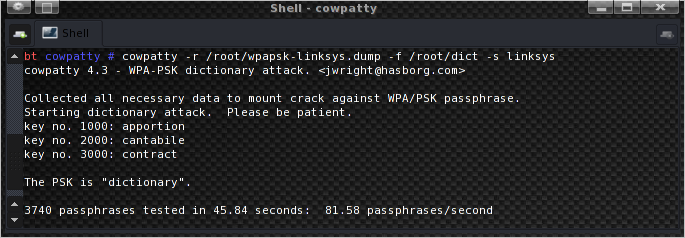
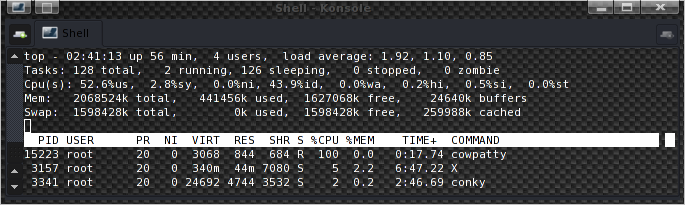
The resulting speed is 81.58 words per second, and as you can see in top, coWPAtty is using only one core.
Test 2 – Dictionary attack on the WPA key with 2 coWPAtty’s running in 2 terms
First we split the supplied word-list into two. The dictionary is about 82 KB big, so the halves will be 41 KB. The command is:
split -b 41k dict
The dictionary is split into two files named xaa and xab.
Now, we’ll open two terminals and run:
cowpatty -r /root/wpapsk-linksys.dump -f /root/xaa -s linksys
and
cowpatty -r /root/wpapsk-linksys.dump -f /root/xab -s linksys
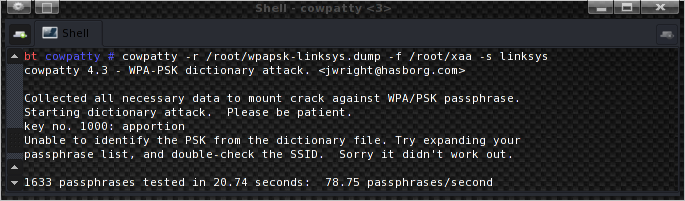
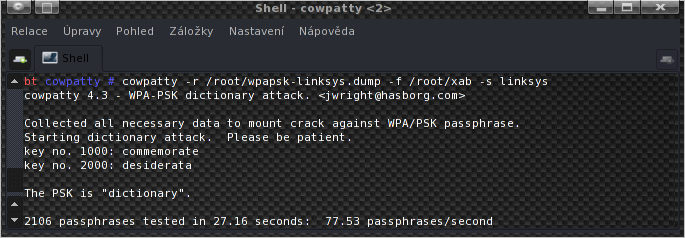
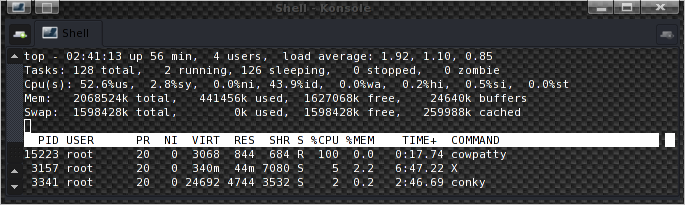
The resulting cracking speed is 78.75 plus 77.53 words per second, so it sums up to 156.28 words/s, and as you can see in the top screenshot, in this case it is using both cores.
Test 3 – airolib-ng
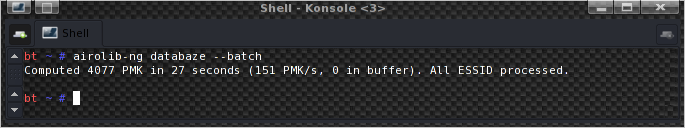
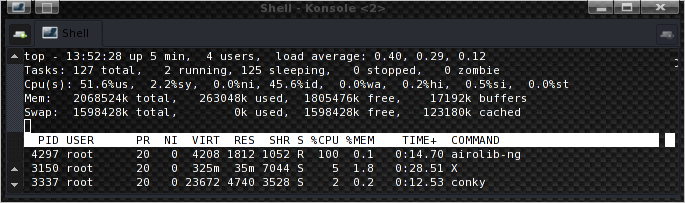
The result: 151 PMK/s.
Test 4 – Two airolib-ng’s running paralelly
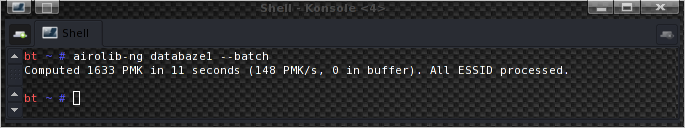
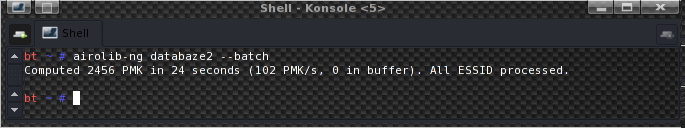
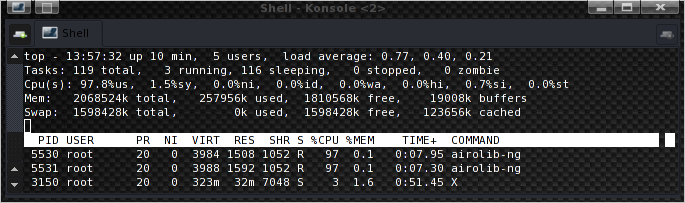
The resulting speeds are 148 PMK/s and 102 PMK/s. Now 250 PMK/s is a pretty nice number, isn’t it?. The 50% difference between the two airolib-ng’s is caused by one imported dictionary being bigger as you can see from the screenshots.
If you have quad-core or some other multi-core, the improvement from using this technique will be of course bigger. You just split the dictionaries in more parts and run more instances of your cracking utility. As they run as separate processes and threads, the system can run each one on the next available core. It might seem a bit cucumbersome, but the result is worth it. Of course it’s up to you, how you use this thread dividing technique. It caught my attention when i read about it and want ed to share it with you. 🙂
For AMP Security, written by Marcos.
Similar Posts:
- Aircrack-ng optimalization for CPU with SSE2
- Cracking WPA-PSK secured Wireless Networks
- How To Kamikaze firmware Linksys WRT54GL
- Complete Google Hacks List
- Installing ipkg & mc (Midnight Commander & more) NAS Synology DS212j
- Airgraph-ng graphing away Wi-Fi traffic
- Naked Edimax EW-7318USg – Photogallery
- Sniffing networks and data analysis
- Evilgrade Toolkit helping with fake updates
- Essential Tools – Nessus exploit and rootkit scanner



1 Diskuze “Utilizing multiple CPU cores for password cracking”