 From the word compound of evil and grade, you see there will be something evil about this piece of software and upgrades. It is a modular framework for supplying clients with fake updates that can contain a wide scale of payloads. The problem of poorly implemented actualization routines has been well know for quite some time now, but it seems it has been greatly overlooked. In the time of creation Evilgrade (summer 2008), very popular software has been vulnerable to this kind of exploit such as
From the word compound of evil and grade, you see there will be something evil about this piece of software and upgrades. It is a modular framework for supplying clients with fake updates that can contain a wide scale of payloads. The problem of poorly implemented actualization routines has been well know for quite some time now, but it seems it has been greatly overlooked. In the time of creation Evilgrade (summer 2008), very popular software has been vulnerable to this kind of exploit such as
Content for ‘Security’
 After demonstrating and still tweaking the nervously expected BackTrack 4 beta at shmoocon, it is now available for download from some number of official mirrors. There are several torrents named bt4 but believe they are full of malware. The Remote-Exploit encourages you to download it directly from them. They have made a big decision on this version – moved from from Slackware to (as we have seen) an Ubuntu server with
After demonstrating and still tweaking the nervously expected BackTrack 4 beta at shmoocon, it is now available for download from some number of official mirrors. There are several torrents named bt4 but believe they are full of malware. The Remote-Exploit encourages you to download it directly from them. They have made a big decision on this version – moved from from Slackware to (as we have seen) an Ubuntu server with
 Cross Site Scripting by Anton Rager. XSS is typically perceived as a minimal threat by many developers and security professionals. There have been some good papers in the past that should have woken folks up to the potential risks of XSS, but the problem is still prevalent and most security folks are not interested in the issue and its ramifications. I hope to change that perception with this paper and the release of a tool called XSS-Proxy that allows XSS attacks to be fully controlled by a remote attacker.
Cross Site Scripting by Anton Rager. XSS is typically perceived as a minimal threat by many developers and security professionals. There have been some good papers in the past that should have woken folks up to the potential risks of XSS, but the problem is still prevalent and most security folks are not interested in the issue and its ramifications. I hope to change that perception with this paper and the release of a tool called XSS-Proxy that allows XSS attacks to be fully controlled by a remote attacker.
 Security conference PACSEC 2008 that will be held in japanese Tokyo on 12th and 13th November 2008 has a great attraction. There will be presented a security research from Mark Tew as a next (not brute force), new implementation of the WPA-TKIP attack. WPA-TKIP security based on the dynamic key generation was supposed to be by laicks and professionals as unbreakable. Much more safe then funny WEP encription.
Security conference PACSEC 2008 that will be held in japanese Tokyo on 12th and 13th November 2008 has a great attraction. There will be presented a security research from Mark Tew as a next (not brute force), new implementation of the WPA-TKIP attack. WPA-TKIP security based on the dynamic key generation was supposed to be by laicks and professionals as unbreakable. Much more safe then funny WEP encription.
 Every press on the keyboard pruduces a small impuls of electromagnetic radiation. This radiation can be captured and easy (quickly) decoded. Even though the described attack effects only some keyboard models it is worth mentioning. Before the penetration test there was done a verification of eleven different keyboards. Each one was reciptive to one of four different methods of availabe attacks. As result see the videos bellow.
Every press on the keyboard pruduces a small impuls of electromagnetic radiation. This radiation can be captured and easy (quickly) decoded. Even though the described attack effects only some keyboard models it is worth mentioning. Before the penetration test there was done a verification of eleven different keyboards. Each one was reciptive to one of four different methods of availabe attacks. As result see the videos bellow.
 Hundreds of programmers, years of development, millions of dollars. If you have installed on your desktop or laptop operating system Windows Vista and you are still thinking that it is the better and more safer system then keep on reading. This small prezentation might change your mind. You probably know an older process with crack NTLM hashe in Windows XP, or changing the password by application CIA commander.
Hundreds of programmers, years of development, millions of dollars. If you have installed on your desktop or laptop operating system Windows Vista and you are still thinking that it is the better and more safer system then keep on reading. This small prezentation might change your mind. You probably know an older process with crack NTLM hashe in Windows XP, or changing the password by application CIA commander.
 With regards to the conference Defcon there has appeared the first publication Subway Hack on internet. The funny thing is that the San Francisco court forbided publishing the material (or even talk about it) just before making the prezentation public at the conference. On the top og it the whole project was removed from the author´s web right after that. Is this a some kind of a honour? Who and why was risking the Streisand effect?
With regards to the conference Defcon there has appeared the first publication Subway Hack on internet. The funny thing is that the San Francisco court forbided publishing the material (or even talk about it) just before making the prezentation public at the conference. On the top og it the whole project was removed from the author´s web right after that. Is this a some kind of a honour? Who and why was risking the Streisand effect?
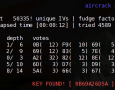
 Last year we told about not so well know tool called MDK, as part of the “Cracking WEP key – Acces Point with pree-shared key (PSK” concept. Alot of time has passed by since then and now we have well workiong stable version even with GUI extension Charon. It was not much of a deal in Fall 2007, but the situation has changed. The autor has also decidedd to eneble the Destruction Mode in the menu.
Last year we told about not so well know tool called MDK, as part of the “Cracking WEP key – Acces Point with pree-shared key (PSK” concept. Alot of time has passed by since then and now we have well workiong stable version even with GUI extension Charon. It was not much of a deal in Fall 2007, but the situation has changed. The autor has also decidedd to eneble the Destruction Mode in the menu.


