 Cross Site Scripting by Anton Rager. XSS is typically perceived as a minimal threat by many developers and security professionals. There have been some good papers in the past that should have woken folks up to the potential risks of XSS, but the problem is still prevalent and most security folks are not interested in the issue and its ramifications. I hope to change that perception with this paper and the release of a tool called XSS-Proxy that allows XSS attacks to be fully controlled by a remote attacker.
Cross Site Scripting by Anton Rager. XSS is typically perceived as a minimal threat by many developers and security professionals. There have been some good papers in the past that should have woken folks up to the potential risks of XSS, but the problem is still prevalent and most security folks are not interested in the issue and its ramifications. I hope to change that perception with this paper and the release of a tool called XSS-Proxy that allows XSS attacks to be fully controlled by a remote attacker.
Security archiv číslo 2
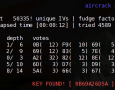 Security conference PACSEC 2008 that will be held in japanese Tokyo on 12th and 13th November 2008 has a great attraction. There will be presented a security research from Mark Tew as a next (not brute force), new implementation of the WPA-TKIP attack. WPA-TKIP security based on the dynamic key generation was supposed to be by laicks and professionals as unbreakable. Much more safe then funny WEP encription.
Security conference PACSEC 2008 that will be held in japanese Tokyo on 12th and 13th November 2008 has a great attraction. There will be presented a security research from Mark Tew as a next (not brute force), new implementation of the WPA-TKIP attack. WPA-TKIP security based on the dynamic key generation was supposed to be by laicks and professionals as unbreakable. Much more safe then funny WEP encription.
 Can your CPU do this? The idea is, I have a notebook and I want to extend the time of working on the nootbook without being pluged into the electric outlet. There are many possibilities how to do it. It definitely means that you have installed linux based operating system. You can save something by taking away modules that are unnecessary for hardware or by reducing the backlight of LCD. And what is the second biggest time glutton right after LCD?
Can your CPU do this? The idea is, I have a notebook and I want to extend the time of working on the nootbook without being pluged into the electric outlet. There are many possibilities how to do it. It definitely means that you have installed linux based operating system. You can save something by taking away modules that are unnecessary for hardware or by reducing the backlight of LCD. And what is the second biggest time glutton right after LCD?
 Every press on the keyboard pruduces a small impuls of electromagnetic radiation. This radiation can be captured and easy (quickly) decoded. Even though the described attack effects only some keyboard models it is worth mentioning. Before the penetration test there was done a verification of eleven different keyboards. Each one was reciptive to one of four different methods of availabe attacks. As result see the videos bellow.
Every press on the keyboard pruduces a small impuls of electromagnetic radiation. This radiation can be captured and easy (quickly) decoded. Even though the described attack effects only some keyboard models it is worth mentioning. Before the penetration test there was done a verification of eleven different keyboards. Each one was reciptive to one of four different methods of availabe attacks. As result see the videos bellow.
 We were able to get pictures of USB wireless card Edimax EW-7318 USg taken to pieces. As you can see on the picture the hack antenna on the modele without connector for external antenna will be trivial. The mother board is at all models the same. If you have an older or “non-antenna” USB WiFi adapter Edimax you can go ahead doing modifications.No need to write more. The card without the driver modification works and injects almost at every Linux distribution.
We were able to get pictures of USB wireless card Edimax EW-7318 USg taken to pieces. As you can see on the picture the hack antenna on the modele without connector for external antenna will be trivial. The mother board is at all models the same. If you have an older or “non-antenna” USB WiFi adapter Edimax you can go ahead doing modifications.No need to write more. The card without the driver modification works and injects almost at every Linux distribution.
 Guide for bios hack of HP laptops in 1.0 :: What´s it about? HP as well as IBM have ona notebooks Whitelist block in bios. That means that if you change the original Wifi card with a new one the BIOS will write this: 104-Unsupported wireless network device detected. System Halted. Remove device and restart. If you contact the Hewlett-Packard customer support they will probably try to satisfy you with advices such as update bios or update driver (as it would be possible to get in any operating system 🙂
Guide for bios hack of HP laptops in 1.0 :: What´s it about? HP as well as IBM have ona notebooks Whitelist block in bios. That means that if you change the original Wifi card with a new one the BIOS will write this: 104-Unsupported wireless network device detected. System Halted. Remove device and restart. If you contact the Hewlett-Packard customer support they will probably try to satisfy you with advices such as update bios or update driver (as it would be possible to get in any operating system 🙂
 Modifying a Bluetooth dongle for an external antenna. BlueTooth is today a standard part of every notebook and a better mobile phone. To bad if you want to do BlueJacking or BlueSnarfing and the bluetooth is in your computer only as a fashion accessory (module glued-on the WiFi card). In that case you have only two possibilities. Take out the pigtail to connect the external antenna. It´s not much fun to make holes into the new laptop. Who has tried it found out
Modifying a Bluetooth dongle for an external antenna. BlueTooth is today a standard part of every notebook and a better mobile phone. To bad if you want to do BlueJacking or BlueSnarfing and the bluetooth is in your computer only as a fashion accessory (module glued-on the WiFi card). In that case you have only two possibilities. Take out the pigtail to connect the external antenna. It´s not much fun to make holes into the new laptop. Who has tried it found out
 Nessus is a security scanner of vulnerability. Lately there was a lot of discussion about this topic. First of all little bit of history. Project Nessus was originaly under GPL licence, but somebody smart has closed the source codes and GPL was over. The project continued as Tenable Nessus and free version (GPL licence) under name GNessUs. But this one died out after a year abd the application goes on as OpenVas. Parallel GPL project is based on the last opened source code
Nessus is a security scanner of vulnerability. Lately there was a lot of discussion about this topic. First of all little bit of history. Project Nessus was originaly under GPL licence, but somebody smart has closed the source codes and GPL was over. The project continued as Tenable Nessus and free version (GPL licence) under name GNessUs. But this one died out after a year abd the application goes on as OpenVas. Parallel GPL project is based on the last opened source code


