 Lets look at an interesting and 100% functional graphic extension for WEP/WPA crack pack of applications, aicrack-ng (airodump-ng, aireplay-ng, aircrack-ng). The application was tested in the reality, in the operating system Ubuntu 10.04 LTS Lucid Lynx. USB WiFi card used for the test is Alfa AWUS050NH. This card was bought thanks to your donations (check out text five wireless adapters for wireless hacking). The used driver is the original part of Ubuntu Linux (rt2800USB). Besides the pack aircrack-ng and MDK3 there are specified for the error free functioning mentioned dependances: gtk-sharp2, libncurses5-dev, monodevelop, libqyoto4.5-cil, qyoto-dev.
Lets look at an interesting and 100% functional graphic extension for WEP/WPA crack pack of applications, aicrack-ng (airodump-ng, aireplay-ng, aircrack-ng). The application was tested in the reality, in the operating system Ubuntu 10.04 LTS Lucid Lynx. USB WiFi card used for the test is Alfa AWUS050NH. This card was bought thanks to your donations (check out text five wireless adapters for wireless hacking). The used driver is the original part of Ubuntu Linux (rt2800USB). Besides the pack aircrack-ng and MDK3 there are specified for the error free functioning mentioned dependances: gtk-sharp2, libncurses5-dev, monodevelop, libqyoto4.5-cil, qyoto-dev.
 The security conference Shmoocon Washington 2010 presentation introduces AirDrop-ng. This 20 minute video presentation show the new Wi-Fi hacking tool. AirDrop-ng is a python based script and is able to do the same as aireplay-ng -0, mdk3 and void11 altogether. It seems that it will be another application in the aircrack-ng suite. As you will see in the video Airdrop-ng is something we should look forward to:-).
The security conference Shmoocon Washington 2010 presentation introduces AirDrop-ng. This 20 minute video presentation show the new Wi-Fi hacking tool. AirDrop-ng is a python based script and is able to do the same as aireplay-ng -0, mdk3 and void11 altogether. It seems that it will be another application in the aircrack-ng suite. As you will see in the video Airdrop-ng is something we should look forward to:-).
 Some of you might have seen other tools for charting the network layout by analyzing captured traffic like EtherApe. Well the aircrack-ng team have worked on a tool of their own called airgraph-ng. Now you cannot expect it to be extra stable right away, but it will definitely help you understand the airodump-ng’s output especialy. You can find it in the aircrack-ng package in the scripts subdirectory as it is a simple python script.
Some of you might have seen other tools for charting the network layout by analyzing captured traffic like EtherApe. Well the aircrack-ng team have worked on a tool of their own called airgraph-ng. Now you cannot expect it to be extra stable right away, but it will definitely help you understand the airodump-ng’s output especialy. You can find it in the aircrack-ng package in the scripts subdirectory as it is a simple python script.
 As the market with CPU has moved to multi-core solutions as a alternative method to increase computation power, intensive computing applications are not adapting to this fact so quickly. A Lot of people still don’t know that the system is not able to split tasks into more threads and distribute the work evenly upon the cores. This task is on the application developer who has to implement the multi-thread supporting mechanism.
As the market with CPU has moved to multi-core solutions as a alternative method to increase computation power, intensive computing applications are not adapting to this fact so quickly. A Lot of people still don’t know that the system is not able to split tasks into more threads and distribute the work evenly upon the cores. This task is on the application developer who has to implement the multi-thread supporting mechanism.
 From the word compound of evil and grade, you see there will be something evil about this piece of software and upgrades. It is a modular framework for supplying clients with fake updates that can contain a wide scale of payloads. The problem of poorly implemented actualization routines has been well know for quite some time now, but it seems it has been greatly overlooked. In the time of creation Evilgrade (summer 2008), very popular software has been vulnerable to this kind of exploit such as
From the word compound of evil and grade, you see there will be something evil about this piece of software and upgrades. It is a modular framework for supplying clients with fake updates that can contain a wide scale of payloads. The problem of poorly implemented actualization routines has been well know for quite some time now, but it seems it has been greatly overlooked. In the time of creation Evilgrade (summer 2008), very popular software has been vulnerable to this kind of exploit such as
 After demonstrating and still tweaking the nervously expected BackTrack 4 beta at shmoocon, it is now available for download from some number of official mirrors. There are several torrents named bt4 but believe they are full of malware. The Remote-Exploit encourages you to download it directly from them. They have made a big decision on this version – moved from from Slackware to (as we have seen) an Ubuntu server with
After demonstrating and still tweaking the nervously expected BackTrack 4 beta at shmoocon, it is now available for download from some number of official mirrors. There are several torrents named bt4 but believe they are full of malware. The Remote-Exploit encourages you to download it directly from them. They have made a big decision on this version – moved from from Slackware to (as we have seen) an Ubuntu server with
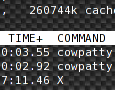
 There is a nice modified version of aircrack-ng I found on their website aircrack-ng.org. It is optimized for CPUs with the SSE2 instruction set (what is SSE2?). For classic dictionary attack on WPA key, it is able to speed things up to 500% compared a not optimized version. I made a test using BackTrack 3 with CPU Intel Core2Duo P8400 2.26 GHz, cowpatty 4.3, aircrack-ng 1.0 rc1 and aircrack-ng-wpa-sse2. For this test I will use a dictionary and a handshake (wpapsk-linksys.dump) from Cowpatty package. The results are on the screenshots.
There is a nice modified version of aircrack-ng I found on their website aircrack-ng.org. It is optimized for CPUs with the SSE2 instruction set (what is SSE2?). For classic dictionary attack on WPA key, it is able to speed things up to 500% compared a not optimized version. I made a test using BackTrack 3 with CPU Intel Core2Duo P8400 2.26 GHz, cowpatty 4.3, aircrack-ng 1.0 rc1 and aircrack-ng-wpa-sse2. For this test I will use a dictionary and a handshake (wpapsk-linksys.dump) from Cowpatty package. The results are on the screenshots.
 Hi everyone. The financing system and the cooperatin surprisingly started to work for you. Thanks to this there was bought or handed few wifi cards so now you can read a comparison of wireless cards in this text. Hopefully it will save you some money in future investments. Buying another hardware is coming soon. So before starting to write I ask you, devoted portal, forum or IRC channel users to stay tuned. More stuff is coming. Tested wireless card, metodic, 5dB omni & 17dB yagi wireless antenna..
Hi everyone. The financing system and the cooperatin surprisingly started to work for you. Thanks to this there was bought or handed few wifi cards so now you can read a comparison of wireless cards in this text. Hopefully it will save you some money in future investments. Buying another hardware is coming soon. So before starting to write I ask you, devoted portal, forum or IRC channel users to stay tuned. More stuff is coming. Tested wireless card, metodic, 5dB omni & 17dB yagi wireless antenna..


