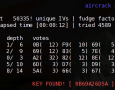
 WLAN Hacking – WPA-PSK handshake. The deauth atack with Aireplay-ng -0 wants to disconect the client from Access Point and after reconnecting get by tapping the handshake. But the process fails. Now what? Be aware that there is another (maybe better and easier) way how to get the data for crack WPA. Wireshark is a strong application and the technology that will be described can be used in other ways like for universal sniffing of the net traffic.
WLAN Hacking – WPA-PSK handshake. The deauth atack with Aireplay-ng -0 wants to disconect the client from Access Point and after reconnecting get by tapping the handshake. But the process fails. Now what? Be aware that there is another (maybe better and easier) way how to get the data for crack WPA. Wireshark is a strong application and the technology that will be described can be used in other ways like for universal sniffing of the net traffic.
Security archiv číslo 4
 Remote-Exploit released BackTrack 3 Final version. Possible downloads are CD image, USB image and VMware image. Links (+ MD5 and SHA1) to download all the version are: CD Image (bt3-final.iso), size 695 MB (MD5: f79cbfbc d25147df 32f5f6df a287c2d9, SHA1: 471f0e41 93136651 7ea8bffe 910fb09a 815e42c7), USB Version (bt3final_usb.iso), size 784 MB (MD5: 5d27c768 e9c2fef6 1bbc208c 78dadf22, SHA1: 3aceedea 0e8e70ff f2e7f7a7 f3039704 014e980f)
Remote-Exploit released BackTrack 3 Final version. Possible downloads are CD image, USB image and VMware image. Links (+ MD5 and SHA1) to download all the version are: CD Image (bt3-final.iso), size 695 MB (MD5: f79cbfbc d25147df 32f5f6df a287c2d9, SHA1: 471f0e41 93136651 7ea8bffe 910fb09a 815e42c7), USB Version (bt3final_usb.iso), size 784 MB (MD5: 5d27c768 e9c2fef6 1bbc208c 78dadf22, SHA1: 3aceedea 0e8e70ff f2e7f7a7 f3039704 014e980f)
 Do you have Z-Comax or other Prism based WiFi card (for example XI-626, XI-325)..? Ubuntu 7.04 Feisty Fawn, same as in the last version Dapper Drake can not do Packet Injection with hostAP driver. This is a short instruction how to change this situation. You need just to download 60MB source code, patch and install dpkg-dev and linux-kernel-devel. Start with creating the folder where the whole operation will run.
Do you have Z-Comax or other Prism based WiFi card (for example XI-626, XI-325)..? Ubuntu 7.04 Feisty Fawn, same as in the last version Dapper Drake can not do Packet Injection with hostAP driver. This is a short instruction how to change this situation. You need just to download 60MB source code, patch and install dpkg-dev and linux-kernel-devel. Start with creating the folder where the whole operation will run.
 I am sure you know the situation. When googling for a technical text the search engine will put together a “great offer” of a book eshop or when looking for a specialized forum you will find an advert for holiday in Spain posted on the first place. Today is almost everyone a “SEO expert” (read lacker) and define the desirable enquiry can be tricky. When the enquiry comes out well – you can be surprised by the results.
I am sure you know the situation. When googling for a technical text the search engine will put together a “great offer” of a book eshop or when looking for a specialized forum you will find an advert for holiday in Spain posted on the first place. Today is almost everyone a “SEO expert” (read lacker) and define the desirable enquiry can be tricky. When the enquiry comes out well – you can be surprised by the results.
 Web pages are protecting it selfs from spammers by system called captcha (Completely Automated Public Turing test to tell Computers and Humans Apart). It is a test that decide if page is viewed by human or bot. Today it’s notorously known. Recongizing symbols from image, counting numbers or decide which picture doesn’t match with others. Captcha shouldn’t require any knowledge from user because that would only decide how much is user educated but doesn’t determine if is huma or not.
Web pages are protecting it selfs from spammers by system called captcha (Completely Automated Public Turing test to tell Computers and Humans Apart). It is a test that decide if page is viewed by human or bot. Today it’s notorously known. Recongizing symbols from image, counting numbers or decide which picture doesn’t match with others. Captcha shouldn’t require any knowledge from user because that would only decide how much is user educated but doesn’t determine if is huma or not.
 After one year of develop the new version of Metasploit Framework released for download. The 3.1 version include a graphical user interface, 450 modules and more than 200 remote exploits. Metasploit runs on Linux, Windows, Mac OS X and BSD. The Windows version of Metasploit includes GUI, console, web interface access, dependencies and networking tools. You can download Metasploit 3.1 version at end of this text. Changelog. Officially using Cygwin for Windows support, Additional stager used for large Windows stages
After one year of develop the new version of Metasploit Framework released for download. The 3.1 version include a graphical user interface, 450 modules and more than 200 remote exploits. Metasploit runs on Linux, Windows, Mac OS X and BSD. The Windows version of Metasploit includes GUI, console, web interface access, dependencies and networking tools. You can download Metasploit 3.1 version at end of this text. Changelog. Officially using Cygwin for Windows support, Additional stager used for large Windows stages
 Cross-Site Scripting is an extensive topic that has been described in the past by several people. Although there is a but. I open a page and start to read a cool text, lots of examples and nice colours all around. But after one hour of reading you are still at the begining. So why after reading AirDump tutorial you should manage XSS in a while? This will be answered in this text called Hacking web applications – XSS. First of all most of the tutorials that can be found on the web are focused on technical and theoretical aspects.
Cross-Site Scripting is an extensive topic that has been described in the past by several people. Although there is a but. I open a page and start to read a cool text, lots of examples and nice colours all around. But after one hour of reading you are still at the begining. So why after reading AirDump tutorial you should manage XSS in a while? This will be answered in this text called Hacking web applications – XSS. First of all most of the tutorials that can be found on the web are focused on technical and theoretical aspects.
 At last there is available a nice piece of hardware – the Hacking WiFi Nets II. – Crack WPA tutorial might be ready even this year, also(?) remake of Linksyse into Wardrive Bot and tutorial Hacking Linksys (extended memory) as planned previously. Access Point Linksys WRT54GL was choosen on purpose. There also exists an upgrade which has the USB port (as well as other AP for example Asus) but then there won’t be nothing to remake.
At last there is available a nice piece of hardware – the Hacking WiFi Nets II. – Crack WPA tutorial might be ready even this year, also(?) remake of Linksyse into Wardrive Bot and tutorial Hacking Linksys (extended memory) as planned previously. Access Point Linksys WRT54GL was choosen on purpose. There also exists an upgrade which has the USB port (as well as other AP for example Asus) but then there won’t be nothing to remake.


