 Wifite v2 support for cracking WPS-encrypted networks (via reaver), v2 new WEP attacks, more accurate WPA handshake capture, various bug fixes. Version 2 does not include a GUI, so everything must be done at the command-line. Designed and tested on Linux; works with Backtrack 5, BlackBuntu, BackBox, and Pentoo! Linux only; no windows or OSX support (but you’re welcome to try). Wifite was mentioned in the New York Times’ article “New Hacking Tools Pose Bigger Threats to Wi-Fi Users” Here is a link to the article.
Wifite v2 support for cracking WPS-encrypted networks (via reaver), v2 new WEP attacks, more accurate WPA handshake capture, various bug fixes. Version 2 does not include a GUI, so everything must be done at the command-line. Designed and tested on Linux; works with Backtrack 5, BlackBuntu, BackBox, and Pentoo! Linux only; no windows or OSX support (but you’re welcome to try). Wifite was mentioned in the New York Times’ article “New Hacking Tools Pose Bigger Threats to Wi-Fi Users” Here is a link to the article.
Katalog ‘wpa-psk’
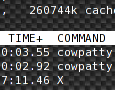 As the market with CPU has moved to multi-core solutions as a alternative method to increase computation power, intensive computing applications are not adapting to this fact so quickly. A Lot of people still don’t know that the system is not able to split tasks into more threads and distribute the work evenly upon the cores. This task is on the application developer who has to implement the multi-thread supporting mechanism.
As the market with CPU has moved to multi-core solutions as a alternative method to increase computation power, intensive computing applications are not adapting to this fact so quickly. A Lot of people still don’t know that the system is not able to split tasks into more threads and distribute the work evenly upon the cores. This task is on the application developer who has to implement the multi-thread supporting mechanism.
 Security conference PACSEC 2008 that will be held in japanese Tokyo on 12th and 13th November 2008 has a great attraction. There will be presented a security research from Mark Tew as a next (not brute force), new implementation of the WPA-TKIP attack. WPA-TKIP security based on the dynamic key generation was supposed to be by laicks and professionals as unbreakable. Much more safe then funny WEP encription.
Security conference PACSEC 2008 that will be held in japanese Tokyo on 12th and 13th November 2008 has a great attraction. There will be presented a security research from Mark Tew as a next (not brute force), new implementation of the WPA-TKIP attack. WPA-TKIP security based on the dynamic key generation was supposed to be by laicks and professionals as unbreakable. Much more safe then funny WEP encription.
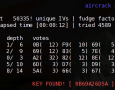
 This is second part of pentesting how to (Ultimate Ubuntu Guide). Lessons from 1 to 9 you can find at How to crack WEP. In this part we ‘ll continue with technique called korek chopchop attack, wep key cracking, aireplay-ng examples, rejects open-system authentication, packetforge-ng, 5GHz band (including frequency and modularity information) , WPA (WPA-PSK) cracking abstrack, connecting to network (gateway, internet) and epilogue
This is second part of pentesting how to (Ultimate Ubuntu Guide). Lessons from 1 to 9 you can find at How to crack WEP. In this part we ‘ll continue with technique called korek chopchop attack, wep key cracking, aireplay-ng examples, rejects open-system authentication, packetforge-ng, 5GHz band (including frequency and modularity information) , WPA (WPA-PSK) cracking abstrack, connecting to network (gateway, internet) and epilogue


