 Archea. It all started connecting four computers in 1969. It followed with trans-antlantic connection between USA and UK, and genesis of TCP/IP (1973). Internet boom was set off internetu by email and protocol www in 1991.
Archea. It all started connecting four computers in 1969. It followed with trans-antlantic connection between USA and UK, and genesis of TCP/IP (1973). Internet boom was set off internetu by email and protocol www in 1991.
It took only 15 years and in the net came into being another paralel world. Lets do a small excursion into the world of “baud beauty”.
The tour-guide and interpreter will be Wireshark (Ethereal), Tcpdump, Cain, Kismet, CommView, AiroPeek, OmniPeek, Netdopler, Ettercap-ng and others.
keywords: net, layer, protocol, routing
bit & packet
The packet includes in every aspects a lot of important information. These information can be seen and read. To understand this topic it is necessary at least a basic knowledge of protocols, coding and hardware.
keywords: bit, Byte, packet, information, latency

Latency
..it is the time beetween sending after receiving the information, packet or set of instrucition. It is probable that part of the communication will be repeated in the net. This happens when its part does not reach the end. How do you know that the data flow was interrupted? Each communication starts, runs and is finished. At the same time every packet is numbered and has its control sum. In case that the line is interrupted or the packet is changed then the data flow is interrupted. The net condition can be infuenced by its administration and its servicing. The aspect that can be measured is its speed, transmission and latency.
ping 10.100.42.19
ping google.com
Promiscuity vs. Monitor Mode
The card in promiscuous mode does not ingnore the packets which do not have in their title its MAC address. After overcoming this barrier the user gets all information in the net (thanks to the right application – sniffer).The Monitor Mode is a similar technique(statute) and can be applied in wireless nets.
Relevant CMD for Linux:
Promiscuity.
iwconfig eth0 promisc
Mode Monitor.
iwconfig eth0 mode Monitor
Mode Monitor – Airmon
airmon start eth0
In Windows the right application can switch the network card into promiscuity. You will find the possibility of switching into promiscuity more often at network card then at wireless cards. Read here what can which network card do.
keywords: hardware, mode, syntax
Packet Injection
Packet Injection is a technique by which the net running can be manipulated, the connection is run away or modifies the packet itself. For this purpose exist individual applications. There are ones where the whole packet can be writen (winject), there are ones which can catch the packet and offer its modification (ethereal, commview) and there are applications fully automated (aireplay-ng, wireshark)
keywords: packet, manipulation, injection, HEX, ASCII, raw
Sniffer
This tool category includes:
1. Easy console application (tcpdump, dsniff)
2. GUI tools (abel & cain) focused on password catching, crack hash.
3. GUI analytical tools (airopeek, omnipeek)
4. Other applications (commview)
Now the most important. There is no difference between an expensive application or simple program. Both kinds o applications can see the same data. Its just up to you how you will filter the data.
keywords: application
Application.
Ethereal, Wireshark, Airodump-ng, Kismet, Tcpdump, Dsniff, AiroPeek, OmniPeek, Netdopler, CommView, Abel & Cain, L0pthCrack, Cowpatty.
keywords: GUI, console
Term & knowhow
When you have more and more used protocols and number of data the filtration gets more difficult. When testing a small local net just check the status or the protocol filtration. When looking for few bits in the flow you will need a more complicated syntaxe and allert.
keywords: bandwidth, filtration, rules (rulez), synatx
Keyword: Keyword
In the internet is every information transfered 1. into plaintext or 2. encrypted. From a normal word,term or protocol title becomes a keyword when we use it for selecting a concrete information. The term we put into google is the Keyword and its the same when filtering in the application or when looking for concrete data in the database, internet, discussion etc. When there is an information overflow you can cleanup the result with a filter.
keywords: keyword, filter, filtration
Filter, Allert
The data are filtered by a set of defined terms (filters) and the result is adjusted by so called keywords. The net running can be analyzed within the protocol in total further according to the direction of the communication, communication volume (regular, error, requested, unrequested), speed, management of data framework and content (message).
Keywords from Protocol
For communication filtering there is necessary a knowledge of keywords. Protocol identification is an essential description of every application which is for internet analysis dedicated. Most often we see
protocols: tcp, udp, dns, dhcp, icmp, arp, smtp, pop3, aim, irc
The protocols are divided into categories and each protocol serves only for existing purpose. (transport, management atd.)
Keys for Password
At autentization, login or autorization we most often see terms:
id, crc, uin, uid, user, userid, user_id, username, member, ulogin, session, account, uname, login, email, webuser, login, logon, upass, password, pass, pw, pwd, passwd.
Wireless nets
Strong and wireless nets run on the same principle. They are only diversified by technological specificity that solve appropriate applications. (filters)
Wireless specificity.
Wireless is administrated within these frames:
Management
– checking connecting and connection quiting.
Controlling
– validation of accepting frames
Data
– including data from the highest layer
Lets just follow the third category – Management frames. They are very complex and offer many possibilities. You will know some terms from Aireplay-ng.
Second management of frames
Association request frame
Association response frame
Reassociation request frame
Reassociation response frame
Authentication frame
Beacon frame
ATIM frame
Probe request frame
Probe response frame
Disassociation frame
Deauthentication frame
Special: Reduction of frame collision.
RTS (Request To Send)
CTS (Clear To Send)
ACK (Acknowledge)
What for is this knowledge? For example.. Ability to detect concrete management frame allows the Kismet application to IDS (attack detection). Few of following Deauth frames does not mean anything else then one of wep atack techniques (thanks to MAC spoofing the atacker enters the communication). See Susspicious trafic, Allert etc. We call this feature IDS. (intrusion detection system).
keywords:source address, destination address, essid, bssid
Airodump-ng
Console application. It is often by mistake considered as sniffer. Its a part of Aircarck-ng package and it is nothing more then classical stumbler. It detects all nets and all connected clients to hand. It knows the statistics and the latest version also detects the wep encryption type. Most often it is used within Aireplay-ng application.
Kismet
Console application. By hitting the key “d” you will see a window with all traffic within the grasp of antenna. It uses Monitor mode and it is a passive snifer. Therefor his presence can not be detected. It can detect about 15 suspicious activities to hand. It is a wardrive / IDS
application.
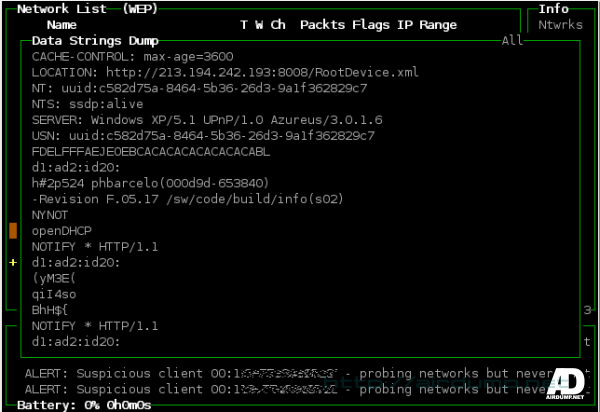
Extract of suspicious activities can be invoked by key w
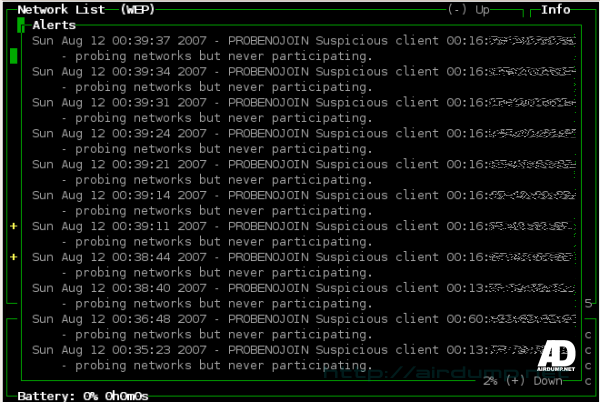
The communication does not have a bigger possibility of filtration. You can use WEP key for realtime decode traffic. It catches and shows IP addresses all connected clients, including detailed information about every eguipment. It has support for GPS modul.
tcpdump
Consol application, easy interface, is a powerful tool in hands of an experienced user. Except some interesting possibilities and filters there is not much more to write about. Outspoken. There is as well a windows version.
To find out if the card is promisc:
ifconfig eth0 | grep -c PROMISC
The whole traffic dump on device:
tcpdump -i eth0 -n
POP3 Password
tcpdump tcp port 110 -X |grep PASS
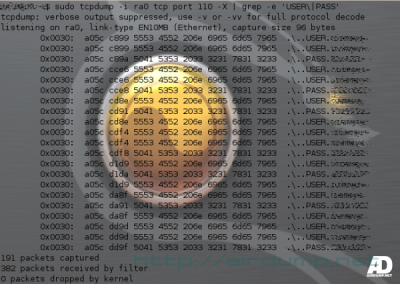
HEX data with defined size.
tcpdump -s 1514 -X
For ASCII instead of -X you can use switch -A, for saving into log switch -w filename
Client in the net:
tcpdump -i eth0 host some-pc
Clients in the net defined by MAC
tcpdump -i eth0 ether host 00:0A:2E:00:0A:2E
For MAC choose from ARP table (ip neigh)
ping -c1 ip ; ip neigh | grep 10.100.52.1
UDP packets shorter then 80 bit:
tcpdump -i eth0 less 80 and ip proto \udp
Dump: Source, direction, port – Explanation
src host IP – packet from IP
dst host IP – packet for IP
host IP – packet from or for IP
src port 80 – packet from port 80
dst port 80 – packet on port 80
port 80 – from or on port 80
These possibilities are highly variable.. Example..
tcpdump -i eth0 src host 10.10.50.1 and dst host 10.10.50.14 and not dst port 80
Explanation:
src net network/mask – source
dst net network/mask – end
Communication between PC in the local knot
tcpdump -i eth0 -n not ether host 00:02:xx:xx:xx:xx
You can use “level flag”:
–v
–vv
–vvv
Dump of line part of frame (MAC source and end, link protocol.):
-e
Communication login on the port 80 and IP address 10.100.xx.xx
tcpdump -vvv -l -w- -A 'host 10.100.xx.xx and tcp port 80'|tee /tmp/logfile
NetDoppler
Aplication from WildPackets are in all aspects universal and higly
configuratable.
Wireshark & Ethereal
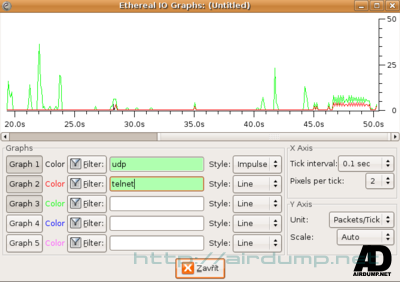
Data filtration can be demostrated using application Wireshark. It can after inserting the right WEP key decode traffic and there is also a patch which allows Wireshark Packet Injection. It also can make diagrams.
Format for inserting WEP & WPA keys in to filter
wpa-pwd:heslo:SSID
wpa-psk:012345678910111213..
wep:b2:c3:d4:e5:f6
Fitration itself can be done manualy or by GUI interface.
Tethereal can be set off in the console.

Other good tools are so called operators..
eq or == Equal
ne or != Not Equal
gt or > Greater Than
lt or > Less Than
ge or >= Greater than or Equal to
le or <= Less than or Equal to
..and logical terms.
and or && Logical AND
or or || Logical OR
not or ! Logical NOT
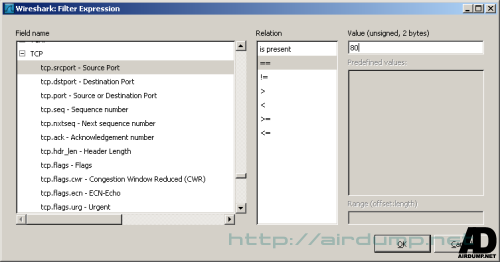
Syntax of the filter is obvious. How to an application sophisticated. The number of filters and their understanding allows detailed investigation of every aspect ot he net.
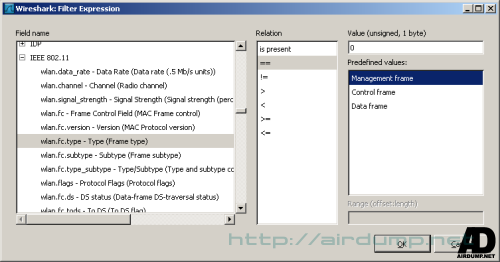
Frame Management. This is a concrete syntax used for management frame filtration.
Association Request
wlan.fc.type_subtype == 0
Association Response
wlan.fc.type_subtype == 1
Probe Request
wlan.fc.type_subtype == 4
Probe Response
wlan.fc.type_subtype == 5
Beacon
wlan.fc.type_subtype == 8
Authentication
wlan.fc.type_subtype == 11
Deauthentication
wlan.fc.type_subtype == 12
The easiest filtration is by key word – Protocol. In the list you can find few of relevant examples of protocol filtering and possible combinations.
DNS
port 53
Telnet
telnet.auth.cmd
AIM ID Question 🙂
aim_icq.owner_uid
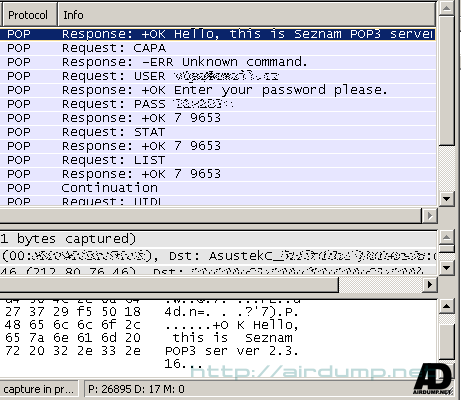
POP3
pop.request
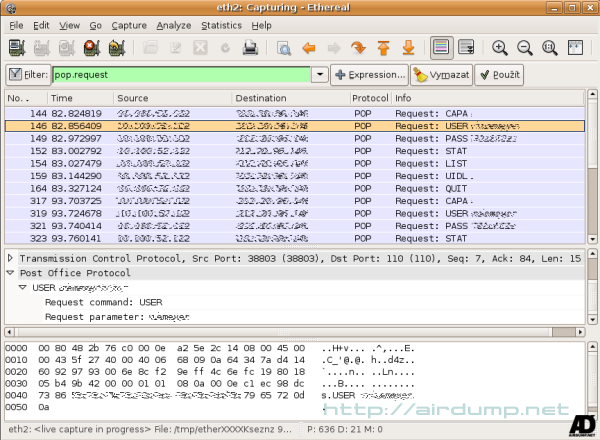
Detail:
Various HTTP
http.content_type[0:4] == "text"
http.request.method == "GET"
http.request.method == "POST"Catches the password on pop3
http contains airdump.net
http.request
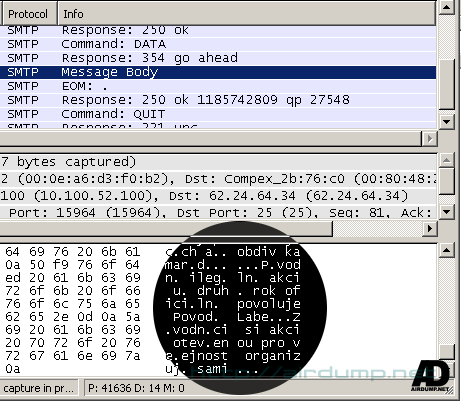
SMTP
smtp.request
Filtration by IP – Source and end.
ip.dst eq airdump.net
ip.src == 192.168.1.1
Both way traffic – IP
host 10.10.150.4
Part of MAC address.
eth.src[0:3] == 00:0e:a2
Some Combination: Protocol, Keyword, IP, value
http and frame[100-199] contains "pass"
tcp.port == 80 and ip.src == 192.168.20.1
ip.addr ne 10.100.52.1
contains – for value
matches – for regular expression
Testing TCP SYN
tcp.flags 0x02
Seclude rules – filtering
not ip or ip.dst ne 224.1.2.3
ip.dst ne 224.1.2.3 – restrictive
Combination
ip.dst eq airdump.net & ip.dst ne 10.100.52.122
ip.dst eq airdump.net & ip.dst ne 10.100.52.12 ip.dst ne 10.100.52.15
MAC Filter
wlan.bssid == 00:18:f8:c5:5d:3e
Rubbish filtering in beacon.
!wlan.fc.type_subtype == 8
wlan.fc.type_subtype != 8
Management Frames Filter
wlan.fc.type == 0
Control Frames
wlan.fc.type == 1
Data Frames
wlan.fc.type == 2
Abel & Cain
Universal tool which main part is named Cain. It has concretely defined possibilities. From 5 important atacks only ARP knows Poisoning. It includes a lot of other tools. (stumbler, crack, dump system passwords, calculation of hashe wpa etc.)
HEX Dump Boot Key
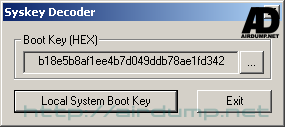
LSA Dump
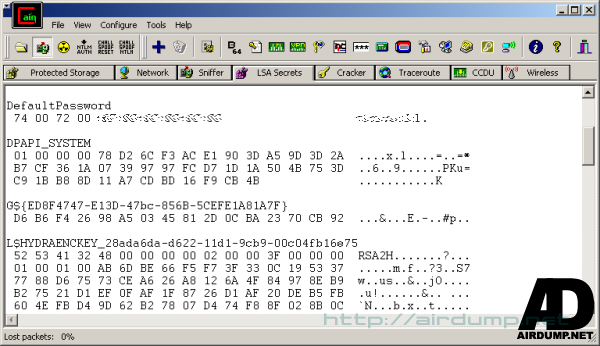
WEP Dump
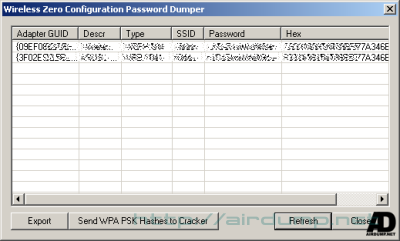
WPA-PSK Calculator
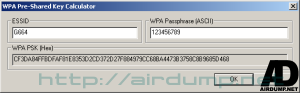
Well arranged and logicaly divided interface and log.
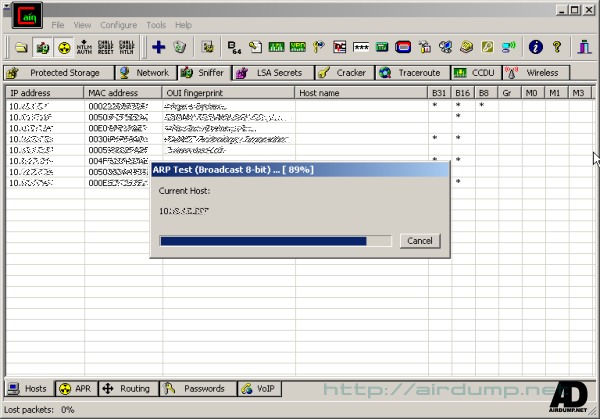
After automatic scan of address range you just mark in the table the required addresses.
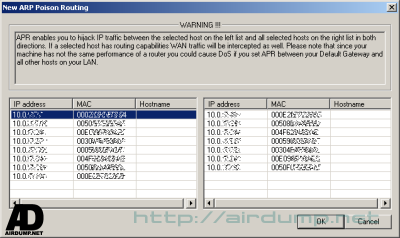
In the ARP fold you can watch routing and the volume of transfered data PC in the net.
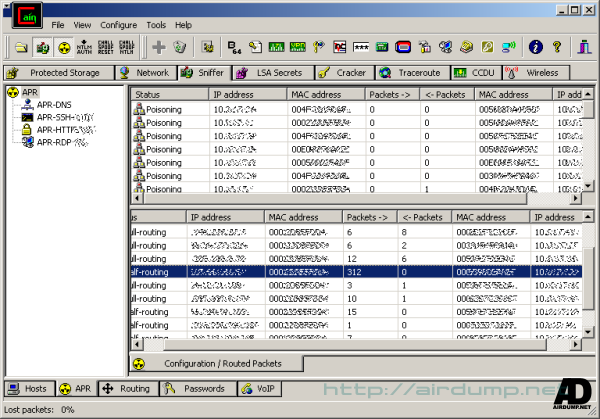
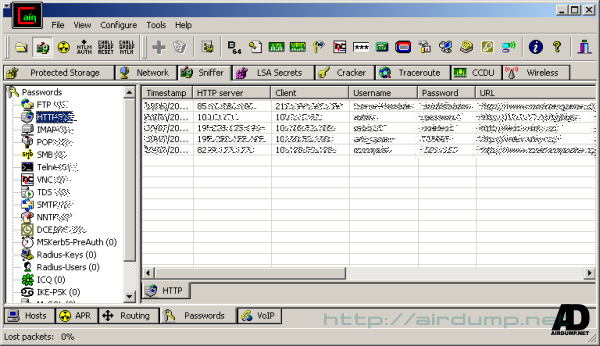
In the next folds catched certificates, voice files, management map static routing or in the Password fold catched password.
The card that does not know promiscuity is in application Abel & Cain for nothing. Distantly you can thanks to Cain install Abel file thanks to you can get on a distant machine a console.
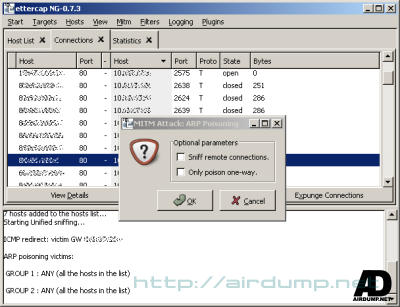
Ettercap-ng
At this time sniffer which implements all described MITM atacks and number of useful plugins. It is easy and user friendly.
Application window shows in the real time all net connections, detailed statistics, active clients it the net.
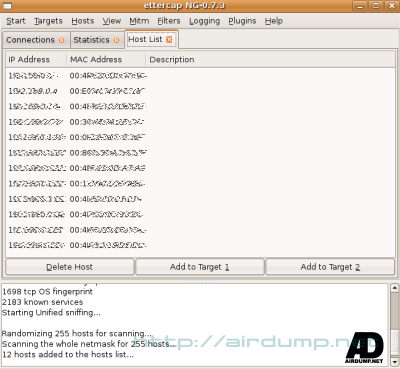
There should not be any complications on MITM panel.
Similar Posts:
- Wireless Hacking – Ultimate Ubuntu Guide
- KoreK chopchop, Kismet, Gateway Ubuntu
- IEEE ICC on Security Technology
- WEP cracking Intel Centrino, OmniPeek + winAircrack
- Capturing WPA-PSK handshake
- BackTrack 5 Wireless Penetration Testing
- Destruction Mode Charon 2 GUI
- Bluetooth Security & Vulnerabilities
- Exploiting with Metasploit – Hacking Windows XP Box
- Aircrack 1.0 BETA .lzm BackTrack


