 How to crack WEP key with Windows XP or Windows Vista. Platform/Operating system: Windows XP Application/Program: CommView Wi-Fi 5.2 build 484 Driver: Tamosoft 3.0.0.53 (Prism 2.5) or Tamosoft 4.2.2.104 (for Atheros). Hardware: PCI Z-Com XI-626 & miniPCI CM9 Meta: Crack WEP key by CommView Wi-Fi WEPKR plugin. This text will be rather short. Application CommView Wi-Fi except clicking does not offer much more fun 🙂
How to crack WEP key with Windows XP or Windows Vista. Platform/Operating system: Windows XP Application/Program: CommView Wi-Fi 5.2 build 484 Driver: Tamosoft 3.0.0.53 (Prism 2.5) or Tamosoft 4.2.2.104 (for Atheros). Hardware: PCI Z-Com XI-626 & miniPCI CM9 Meta: Crack WEP key by CommView Wi-Fi WEPKR plugin. This text will be rather short. Application CommView Wi-Fi except clicking does not offer much more fun 🙂
Driver
The application will not run without driver that are included. Therefor it is neccesary to update the driver firstly. The card Atheros with the driver from Tamosoft is fully functional and you can control it even outside the application. However Z-Com XI-626 is not so after the test refresh the original driver.

With CommView the .inf for all suported cards are being installed se instaluji (folder Driver.
How to install the driver find in tutorial OmniPeek & ipw3945.
WEPKR Plug-in
This plug-in is a small 300kB application which can be just copied into CommView Wi-Fi slozky. For this test the plug-in version 1.1.0.27 was used.
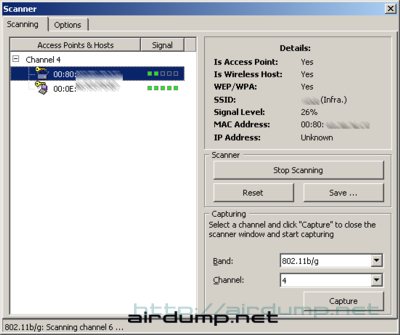
Scanning & Detection
The application is higly configurable and intuitive. The first button invokes the dialog window that offers scan or directly startup capture.
Packet Capture
After Capture startup the dialog closes and makes accessible the first card of the main window of application CommView. There are all relevant information well-arranged sequenced.
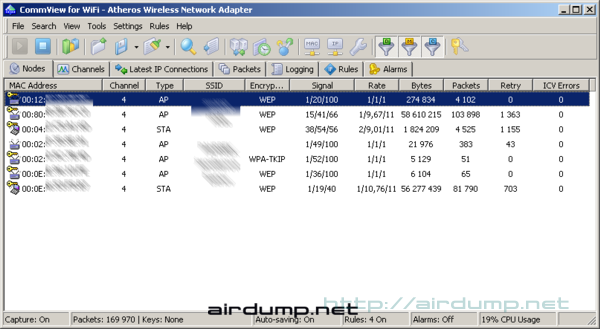
Rullez
On the sixth flag Rules we set at least packet filtration according to MAC address AP that we test.
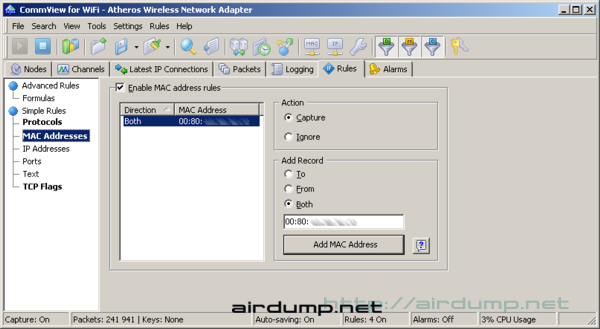
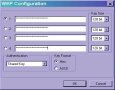
WEPKR Config
The initial plugin konfiguration is sufficient. If you feel like experimenting do not look for konfiguration dialog in application CommView. It is integrated straight in the menu of the window WEPKR plugin. This can be startup through Tools/WEPKR
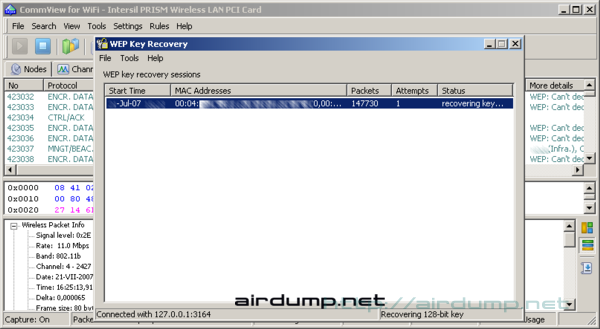
WEP key crack
The key crack itself can be timed according to WEPKR configuratoin or you can startup the plug-in at the start and hope that the application will manage everything itself(will not freeze).
Default configuration after plugin activation will do the first test at the 64 bit key after gathering 100 000 ivs, at 128 bit key 800 000 and at 256 bit key at 1 000 000 ivs. Default setting is 64 bit key/100 000.
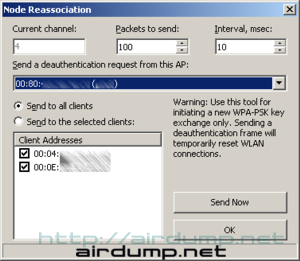
Node reassociation
In menu Tools you will find “reasociation feature”. From its name it is obvious what for it is but it did no do anything fabulous.
Crack WEP
After 30 minutes the plugin WEPKR was set off and the log was imported.
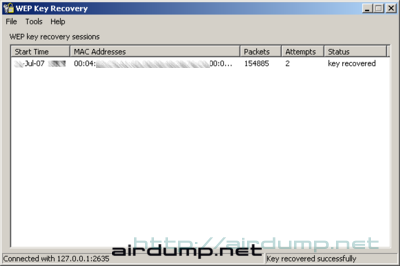
After a minute it is sure that it is not the right time yet. Unsuccessfull trial is shown on the dialog list at the bottom part of WEPKR window. A number is added to the columm Attempts. After another 30 minutes the application was stoped and it was repeated. The sekond result was suprising 🙂 From the oveall amount of 1 500 000 packets about 150 000 of them were ivs. This number was enough for cracking 128 bit WEP key.
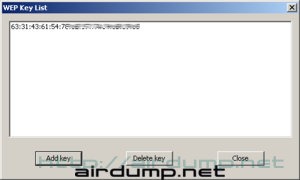
Quarry of the WEP Key
Quite interesting is digging for the WEP key itself. After successfull cracking it does not display. You can find it in the menu and can be displaied after invoking the window (menu) WEP Key List. It can not be copied from the window and is in HEX. Probably a very quick finishing process worth 500$.
Notes
Panic: None of Tamosoft driver versions for Atheros did work properly. I have tested it on CM9 miniPCI and it has frozen every five minutes. After restart it is working for couple of minutes and then it happens again. Prism 2.5 card works without trouble the whole hour.
Similar Posts:
- Aireplay-ng Packet Injection Windows CommView Hack
- The Wireless Adapters and Applications
- Essential Tools – Nessus exploit and rootkit scanner
- XSS pentest plug in – Cross-Site Scripting
- Intel Centrino Packet Injection WiFiSlax and ipw3945
- Capturing WPA-PSK handshake
- Testing 5 wireless cards for wifi hacking
- WEP Crack – video tutorial for beginners
- The Intuitive WiFi hacking GUI app for Ubuntu Linux
- Hewlett-Packard BIOS hacking


