 Security conference PACSEC 2008 that will be held in japanese Tokyo on 12th and 13th November 2008 has a great attraction. There will be presented a security research from Mark Tew as a next (not brute force), new implementation of the WPA-TKIP attack. WPA-TKIP security based on the dynamic key generation was supposed to be by laicks and professionals as unbreakable. Much more safe then funny WEP encription.
Security conference PACSEC 2008 that will be held in japanese Tokyo on 12th and 13th November 2008 has a great attraction. There will be presented a security research from Mark Tew as a next (not brute force), new implementation of the WPA-TKIP attack. WPA-TKIP security based on the dynamic key generation was supposed to be by laicks and professionals as unbreakable. Much more safe then funny WEP encription.
According to the references Mark Tew and Martin Beck will present a way how to pass TKIP (Temporal Key Integrity Protocol).
That is know as the one that uses a dynamic key generation for each of data block.
Paper say.. the time needed for successful WPA cracking is 12 to 15 minutes!
So don’t forget to check fresh materials from the PACSEC 2008 conference website or another internet sources.
The details form the WPA broken Pacsec 2008 conference will be published also here at Remote Security website, probably in the new topic or in the news.
Topics presented at PacSec conference
Putting an SSH server in your NIC – Arrigo Trulzi
Gone in 900 Seconds, Some Crypto Issues with WPA – Erik Tews
Browser Memory Protection Bypasses: Virtual Machines – Mark Dowd, IBM
Cross domain leakiness: Divulging sensitive information and attacking SSL sessions – Chris Evans & Billy Rios, Google, Microsoft
Flash XSS – Rich Cannings, Google
Malicious origami in PDF – Fredric Raynal, Guillaume Delugre
Security for Virtual and Physical Server Environment – Akiko Takahashi
Living in the RIA World (Flash/Air, Silverlight, Gears, Prism, BrowserNow, HTML5) – David Thiel, iSec
Understanding Cross-Domain Models and Threats – Peleus Uhley, Adobe
Gaining access through Kerberos – Emmanuel Bouillon
A new web attack vector: Script Fragmentation – Stephan Chenette, WebSense
Countermeasure to SSH Brute Force Attack according to behaviour – Tetsuo Handa
Advances in Automated Attack Planning – Carlos Sarraute & Alejandro David Weil, Core
Inside “Winnyp”, Winnyp Internals and Concepts of Network Crawling – Toshiaki Ishiyama, Fourteenforty
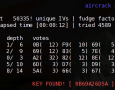
Aircrack-PTW
It was released a better and faster implemantation for breaking WEP secutiry known as Aircrack-PTW. New minimum of the IV’s neede for successful 128 bit key recovery is 19 000 IV. Source code available at SVN. All tools are at your disposal at rootu. The implementaion is of course in the latest SVN version Aircrack-NG.
Similar Posts:
- Aircrack-ng optimalization for CPU with SSE2
- Wifite WEP & WPA password key cracker
- MiFare Subway Hack
- ShmooCon 2008
- Backtrack 3 installation – USB flash memory
- Breaking CAPTCHA protection
- Make your own video tutorial
- Destruction Mode Charon 2 GUI
- Airgraph-ng graphing away Wi-Fi traffic
- AirDrop-ng video presentation – security conference Shmoocon 2010


